Waterfall Security Solutions Resources
Featured
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
INFOGRAPHIC
Discover how Cyber-Informed Engineering's methodology offers an encompassing approach to OT security. Andrew Ginter spoke on our webinar about the proactive approach of Cyber-Informed Engineering and how it enhances the benefits of AVEVA PI.
READ MORE |
 |
RESOURCES
About Waterfall Security Solutions and how they deliver
complete cybersecurity and operational efficiency.
READ MORE |
 |
 |
REPORT
Traditional firewalls were not designed to protect today’s industrial and operational technology environments. This report reveals 13 real world ways attackers bypass firewalls in OT networks and what organizations can do to stop them before critical operations are disrupte...
READ MORE |
 |
ARTICLE
Explore the Cross Domain Solutions (CDS) that securely exchange information across networks of varying trust levels to determine which best protects your organization from data theft, malware and intrusion.
READ MORE |
 |
ARTICLE
Discover the 10 most impactful cyber-attacks in 2024 and how Waterfall's suite of solutions can protect critical environments against these threats.
READ MORE |
 |
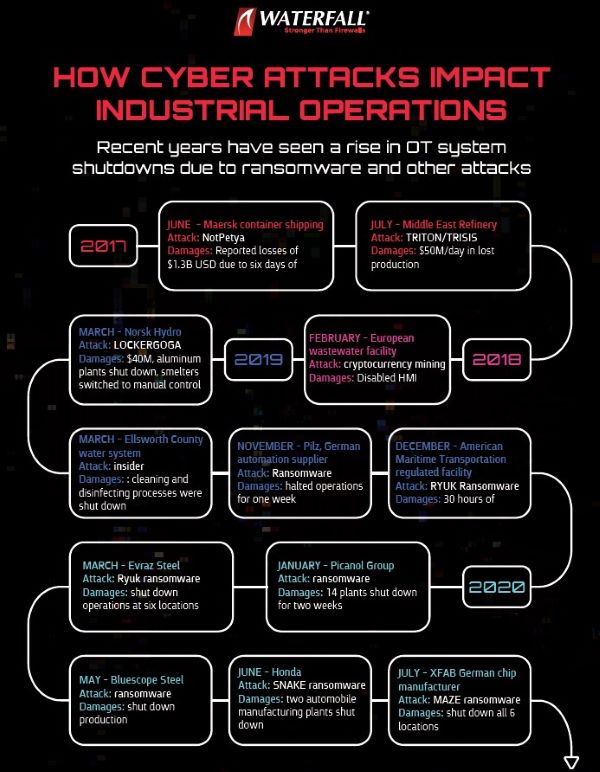
INFOGRAPHIC
Explore recent cyberattacks and their impacts on industrial organizations to better protect your OT network from ransomware threats.
READ MORE |
 |
ARTICLE
HERA, Waterfall Security’s new way of revolutionizing how secure remote access works for OT.
READ MORE |
 |
CASE STUDY
Analyze Waterfall’s Unidirectional Solution for a Government Security Agency wanting to enable real-time transfer of arbitrary files from open-source networks via file, HTTP and email transfers to a secure network environment.
READ MORE |
 |
EBOOK
Download this report to gain insights into how IT network attacks can critically impact OT systems and access expert perspectives on current and emerging cyberthreats.
LEARN MORE |
 |
BLOG
Hear from CEO and Co-Founder of Waterfall Security, Lior Frankel Waterfall Security as Waterfall introduces HERA – Hardware Enforced Remote Access that is designed to enable safe and secure remote access into OT networks and cyber-physical systems.
READ MORE |
 |
EBOOK
Discover how Waterfall Security Solutions robust Unidirectional Security Gateways ensure physical protection against information theft and critical network sabotage. Click here to access this e-book.
LEARN MORE |
 |
BLOG
Waterfall Security Solutions own, Andrew Ginter, discusses Unidirectional Security Gateways and how Waterfall set the standard for secure IT/OT and OT/cloud integration in this blog. Discover how these solutions facilitate secure IT/OT integration and safeguard physical, operatio...
READ MORE |
 |
RESOURCES
Discover the cyber risks facing AVEVA PI servers with increased connectivity and suggests using Waterfall’s Unidirectional Security Gateways for strong protection against online threats.
READ MORE |
 |
CASE STUDY
Waterfall Security Solutions partners with Énergie NB Power to prevent cyberattacks by providing security, visibility, compliance and reduced operational costs.
READ MORE |
 |
CASE STUDY
Waterfall Security Solutions’ Unidirectional Security Gateways protect the OCC network perimeters to maintain the highest level of safety and security from cyber attacks impacted by rail systems.
READ MORE |
 |
CASE STUDY
Detroit’s IT/OT firewall was replaced with Waterfall Security Solutions Unidirectional Security Gateway to eliminate all possible threats penetrating operations from external networks, as well as lowering costs at an estimated $7 Million per year.
READ MORE |
 |
CASE STUDY
Discover how the installation of Waterfall Security Solutions Unidirectional Gateway between the Process Control Network (PCN) and the Enterprise Network provides 100% security, visibility and compliance.
READ MORE |
 |
CASE STUDY
The third iteration of the US TSA Security Directive Pipeline 2021-02C (SDP-2021-02C) takes a more generalized approach compared to the initial two versions, and this has both positive and negative implications.
On the positive side, the broader phrasing of requirements allows...
READ MORE |
 |
CASE STUDY
The abrupt shutdown of the Colonial Pipeline took senior decision-makers by surprise. The pipeline was halted as a precautionary measure due to a compromised IT network, despite no evidence of the ransomware affecting the OT network. Prior to this incident, senior decision-makers...
READ MORE |
 |
PODCAST
We discuss a fresh approach outlined by the US Department of Energy, known as Cyber Informed Engineering (CIE). It’s an approach that focuses on impenetrable safety measures, manual controls, and robust engineering safeguards that are added to the existing and conventional ...
LEARN MORE |
 |
EBOOK
Cyberattacks are no longer a threat, but a painful and costly reality. Simultaneous “cybercatastrophic” attacks against multiple targets with widespread consequences have been estimated to incur between $243B and $1T USD per attack. Many insurance providers respond to...
LEARN MORE |
 |
EBOOK
BSEE has issued the Well Control Final Rule to consolidate existing well control rules into a revised regulation that addresses Blow Out Preventer (BOP) system design, performance and reliability. Operators will be required to gather, monitor and transmit to a monitoring onshore ...
LEARN MORE |
 |
BLOG
In the ever-evolving landscape of cybersecurity, organizations face an unrelenting barrage of sophisticated cyber threats. As the techniques employed by malicious actors become increasingly sophisticated, the need for robust defense mechanisms and thorough investigation methods b...
READ MORE |
 |
BLOG
Uptime is a very important Key Performance Indicator (KPI) for data centers, and the physical infrastructures in data centers are essential to uptime – electric power systems, backup power, fire suppression, physical access control, cooling and more. Managing cybersecurity ...
READ MORE |
 |
INFOGRAPHIC
Sophisticated, targeted ransomware attacks shutting down OT systems and critical infrastructure have gained considerable momentum in recent years. How can you stay ahead of the threat environment and ensure all systems are a go, even if your IT networks are infected? What could t...
READ MORE |
 |
INFOGRAPHIC
What cyber crime threats to oil & gas infrastructures are top of mind for government and business leaders?
Our exclusive infographic explores the top 6 cyber attacks on oil & gas industries in the last decade. From the Shamoon incident that erased 30,000 computers to l...
READ MORE |
 |
INFOGRAPHIC
As data centers grow in importance, scale, and complexity, so do the security challenges they face. Among the various security challenges data centers regularly address, the threats to Operational Technology (OT) and Industrial Control Systems (ICS) – otherwise known as the...
READ MORE |
 |
EBOOK
The NIS2 Directive is an updated EU cybersecurity law that builds on the original NIS Directive (NISD). The goals of NIS2 are to boost cybersecurity, simplify reporting, and create consistent rules and penalties across the EU. By expanding its scope, NIS2 requires more businesses...
LEARN MORE |
 |
CASE STUDY
Waterfall COTS solutions fit into any network architecture. The Unidirectional Security Gateway provides protection from remote cyber threats. To learn how Waterfall’s Unidirectional gateway technology deploys at customer sites, download this resource.
READ MORE |
 |
EBOOK
This eBook from Andrew Ginter of Waterfall Security Solutions and Gregg Hale of ICSSTRIVE, covers cyber attacks with physical consequences in process and discrete manufacturing industries more than doubled from the year 2020 to 2021. Almost all reported incidents were the result ...
LEARN MORE |
 |
EBOOK
Firewalls are used in industrial networks and throughout enterprise networks, but usually require at least one layer of unidirectional gateway technology. Many security practitioners assume that a unidirectional gateway is some sort of “unidirectional firewall”. To compare the ef...
LEARN MORE |