Explore Thales TCT's Self-Guided Tours
Thales TCT and Carahsoft have partnered together to provide a series of self-guided tours of Thales TCT's products and features. Similar to a live demo, the self-guided tours explores how Thales TCT's products and features applies to a specific technology vertical such as Cybersecurity and Zero Trust.
Learn about Thales TCT's benefits, watch a short pre-recorded demo video, and download related resources. If interested in furthering the conversation, you can also schedule a live demo with a Thales TCT expert from Carahsoft. Start a Self-Guided Tour now by selecting one below:
Thales offers SafeNet Trusted Access, a cloud-based access management and authentication service that embodies Zero Trust principles. With a ‘verify everywhere, trust no one’ approach, SafeNet Trusted Access dynamically enforces access decisions at the application access point, irrespective of user location, device used or network routing. Thales emphasizes a ‘default deny’ policy by continuously reassessing and verifying credentials at each login, enhancing security even with Single-Sign-On (SSO) features enabled.
Thales Trusted Cyber Technologies (TCT) provides high-assurance data security solutions aligning with foundational pillars of Zero Trust outlined by CISA. Thales TCT’s authentication, encryption and key management solutions address identity, device, network, application workload and data security aspects, enabling agencies to establish robust Zero Trust architectures
Want to learn more about Thales?
Start a self-guided demo now to learn more about secure remote operations and safeguarding critical data across cloud and hybrid environments with Thales.
Thales' Benefits Snapshot:
-
Secure Remote Work: Enables secure and convenient remote access for employees, contractors and consultants, ensuring a seamless login experience regardless of location or device.
-
Cloud Security: Overcome legacy security limitations by securing cloud applications at the access point, safeguarding data and identities in the cloud environment.
-
Data Protection: Protect applications and data by encrypting information and continuously validating user identities, minimizing the risk of breaches and ensuring data integrity.
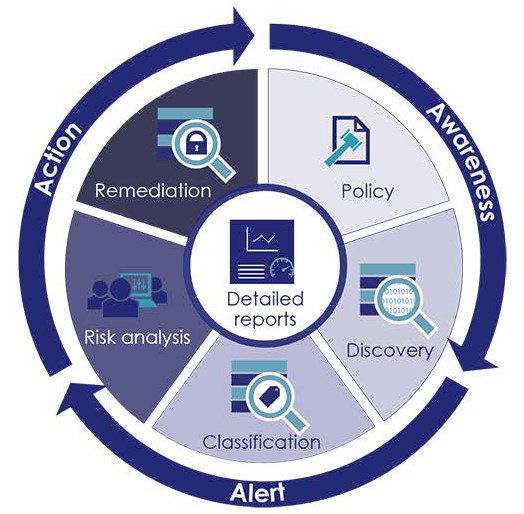
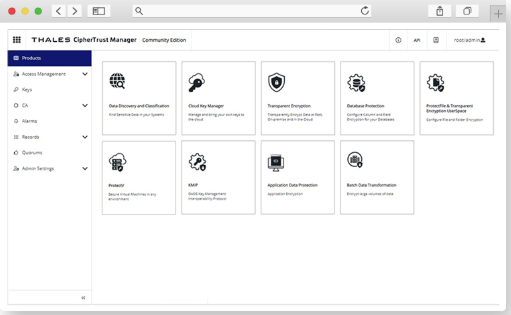
Thales provides a comprehensive Data Security Platform that empowers organizations to safeguard sensitive information and meet compliance mandates across diverse systems and environments. Whether protecting against privileged user abuse, encrypting database data or addressing cloud security requirements, Thales delivers tailored solutions to secure critical assets.
By moving beyond siloed encryption and crypto management tools, Thales offers centralized, uniform data protection with advanced capabilities like data discovery, encryption, key management and hardware security modules. Designed for on-premises, cloud and hybrid IT environments, Thales ensures organizations maintain control of their data, address evolving security challenges and achieve compliance efficiently and cost-effectively.
Want to learn more about Thales?
Start a self-guided demo now to learn more about data security and encryption.
Thales TCT Benefits Snapshot:
- Evolving Threat Defense: Ensure data confidentiality, integrity and availability against emerging threats with Thales Data Protection.
- Enhanced Compliance: Achieve compliance with scalable, high-performance security solutions.
- Cost Efficiency: Reduce costs and boost productivity with integrated, comprehensive protection tools.