Explore Ping Identity's Self-Guided Tours
Ping Identity and Carahsoft have partnered together to provide a series of self-guided tours of Ping Identity's products and features. Similar to a live demo, the self-guided tours explores how Ping Identity's products and features applies to a specific technology vertical such as Zero Trust.
Learn about Ping Identity's benefits, watch a short pre-recorded demo video, and download related resources. If interested in furthering the conversation, you can also schedule a live demo with a Ping Identity expert from Carahsoft. Start a Self-Guided Tour now by selecting one below:
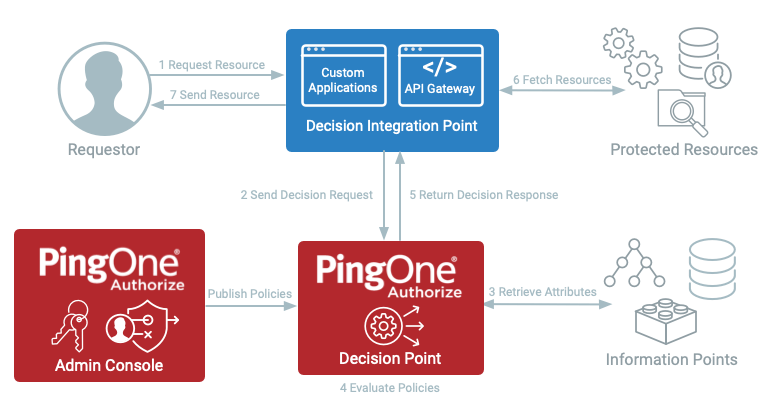
Ping Identity is a leading provider of identity and access management solutions, offering a critical foundation for implementing Zero Trust architectures. Identity is at the core of Zero Trust, and Ping Identity specializes in establishing robust identity control planes that enable agencies to define precise access policies and safeguard critical resources effectively. By modernizing identity, authentication, authorization and monitoring components through standards-based solutions, Ping Identity empowers agencies to break down silos, enhance security and implement Zero Trust architectures seamlessly.
Ping Identity’s solutions elevate the authentication and authorization process from a mundane transaction to a pivotal aspect of identity-centric security strategies. This transformation enables agencies to make risk-based decisions across all access attempts, ensuring protection for vital workforce assets and reinforcing a comprehensive Zero Trust framework that aligns with modern security demands.
Want to learn more about Ping Identity?
Start a self-guided demo now to learn more about security posture, Zero Trust initiatives and digital transformation.
Benefits:
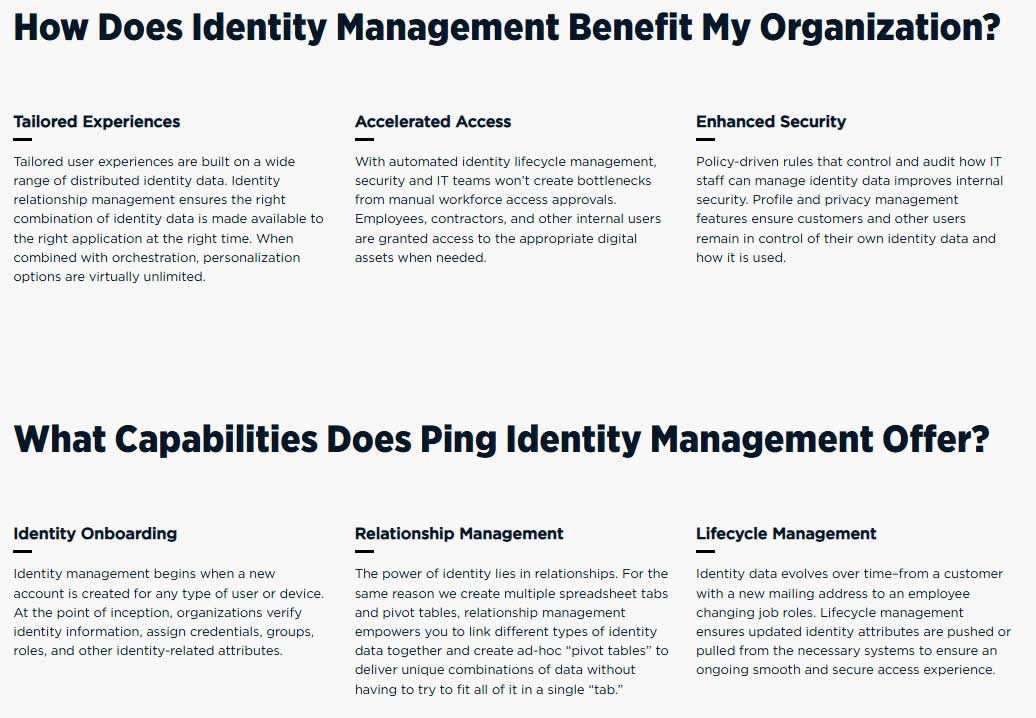
- Enhanced Security: Establish robust identity control planes, facilitating precise access policies and protecting critical resources against unauthorized access attempts
-
Modernized ICAM: Modernize legacy Government ICAM systems, accelerating cloud transformation and enabling secure interoperability across agencies, industries and mission partners.
-
Seamless Zero Trust Implementation: Establish trust boundaries and enforce security policies effectively across hybrid IT environments through Zero Trust architectures.