Data Center Networking Solutions for the Public Sector
Broadcom Inc. is a global technology leader specializing in semiconductor and infrastructure software solutions. Broadcom's industry-leading solutions portfolio provides data center networking and storage, and enterprise and mainframe software designed to meet the unique needs of the Public Sector. Leveraging advanced tools for automation, monitoring, and cybersecurity, Broadcom's offerings empower organizations to protect sensitive information, optimize resources, and meet compliance requirements with confidence.
In partnership with Carahsoft, Broadcom delivers cutting-edge technology from industry leaders Symantec, Carbon Black, CA Technologies, and VMware, ensuring organizations have access to reliable, scalable, and secure technology that supports mission-critical operations. Together, Broadcom brings the size, scope and engineering talent to lead the Public Sector industry into the future.

Strengthen Security with Symantec and Carbon Black
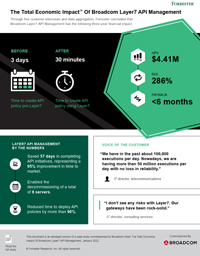
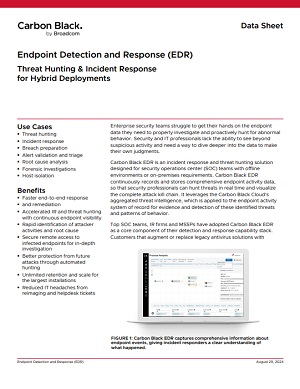
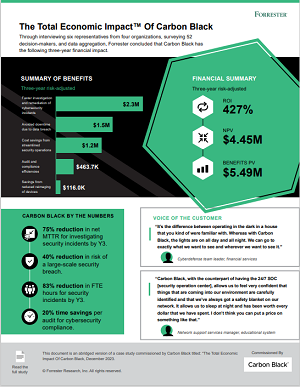
Protect critical data against sophisticated cyber threats with Symantec and Carbon Black cybersecurity solutions. Secure your endpoints, network, email, cloud applications and data—all while maintaining compliance with strict security standards. Learn how Symantec’s advanced threat protection and Carbon Black’s pioneering endpoint defense can bolster your security posture.
Streamline Operations with CA Technologies
Public sector organizations are under pressure to deliver efficient, secure and scalable services. CA Technologies offers powerful AI solutions to optimize network operations, centralized identity and access management, and unify automation observability. Empower your IT team to enhance operational performance, ensure compliance, and meet evolving digital demands.
Transform Public Sector Networks with VMware
VMware by Broadcom enables agencies to build, secure, and scale on-premises cloud environments, delivering comprehensive management to datacenter administrators and self-service infrastructure to developers and app owners. VMware Cloud Foundation with vDefend helps organizations easily address the most common cybersecurity threat vectors and fulfill the need for robust and reliable digital operations. Agencies benefit from the improved performance, increase in mission productivity, and streamlined compliance.