Explore Forescout's Self-Guided Tours
Forescout and Carahsoft have partnered together to provide a series of self-guided tours of Forescout's products and features. Similar to a live demo, the self-guided tours explores how Forescout's products and features applies to a specific technology vertical such as Cybersecurity and Zero Trust.
Learn about Forescout's benefits, watch a short pre-recorded demo video, and download related resources. If interested in furthering the conversation, you can also schedule a live demo with a Forescout expert from Carahsoft. Start a Self-Guided Tour now by selecting one below:
Forescout specializes in cybersecurity solutions, offering comprehensive capabilities for network security, risk management and threat detection. Forescout’s platform enables seamless collaboration with ecosystem partners, empowering Government IT professionals to protect data secure access to resources and ensure compliance for Federal agencies and Public Sector entities. With a proven track record in major Government programs like Continuous Diagnostics and Mitigation (CDM), Forescout is dedicated to safeguarding critical operations and citizens’ daily lives from cyber threats.
Want to learn more about Forescout?
Start a self-guided demo now to learn more about Forescout’s comprehensive capabilities that address the evolving cyber threat landscape.
Forescout’s Benefits Snapshot:
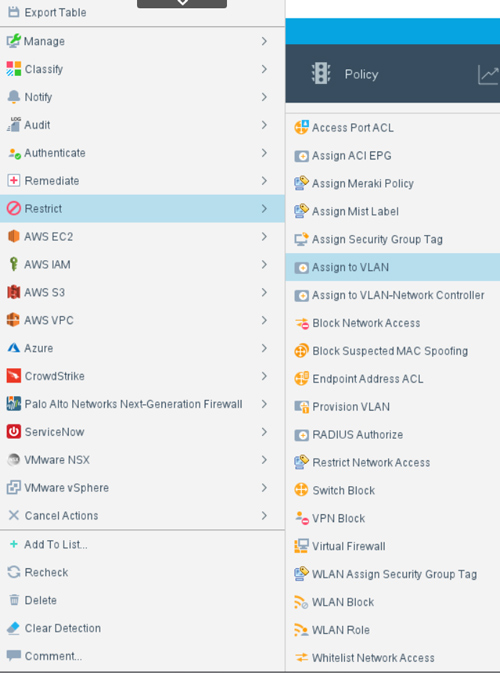
- Access Control- Achieve a Zero Trust architectural framework and limit access to information as well as service and application resources.
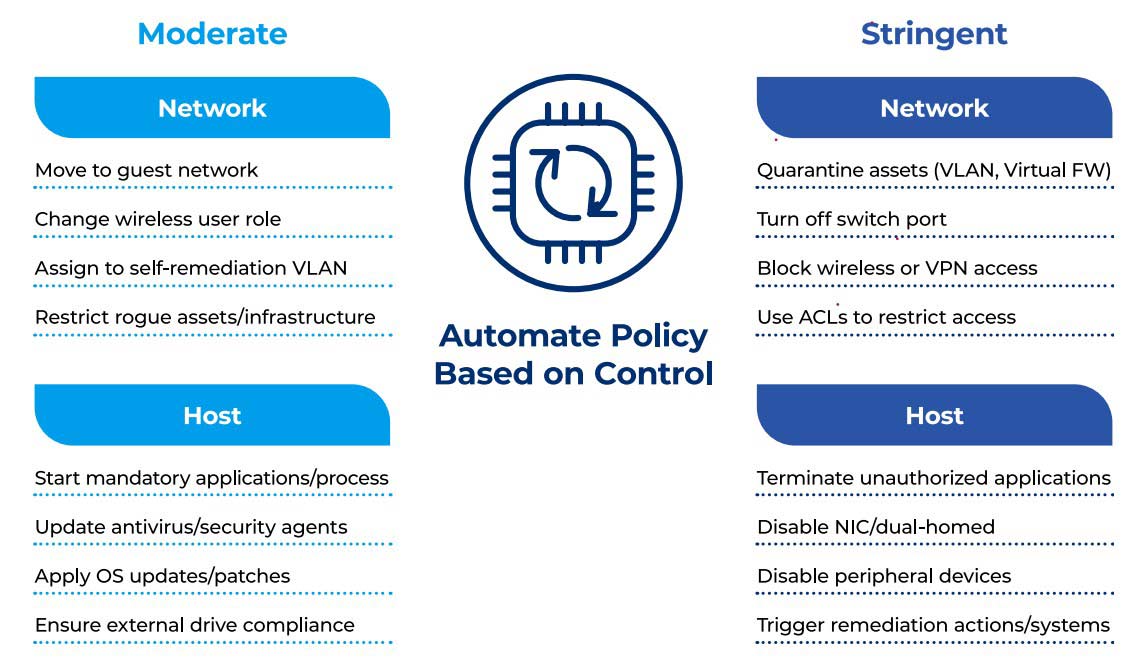
- Incident Response- Understand all connected devices to determine impact of known vulnerabilities and automate mitigation response, reducing time to repair and saving labor.
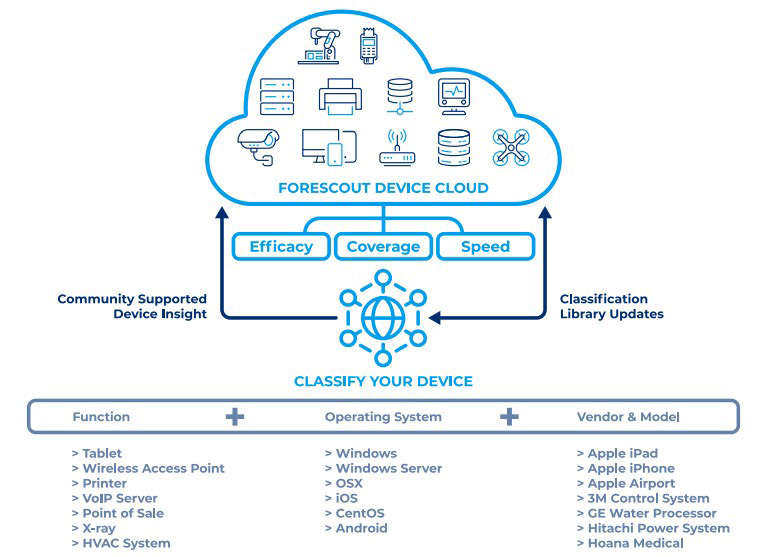
- Supply Chain- Gain insight into embedded software and applications running on managed and unmanaged devices.
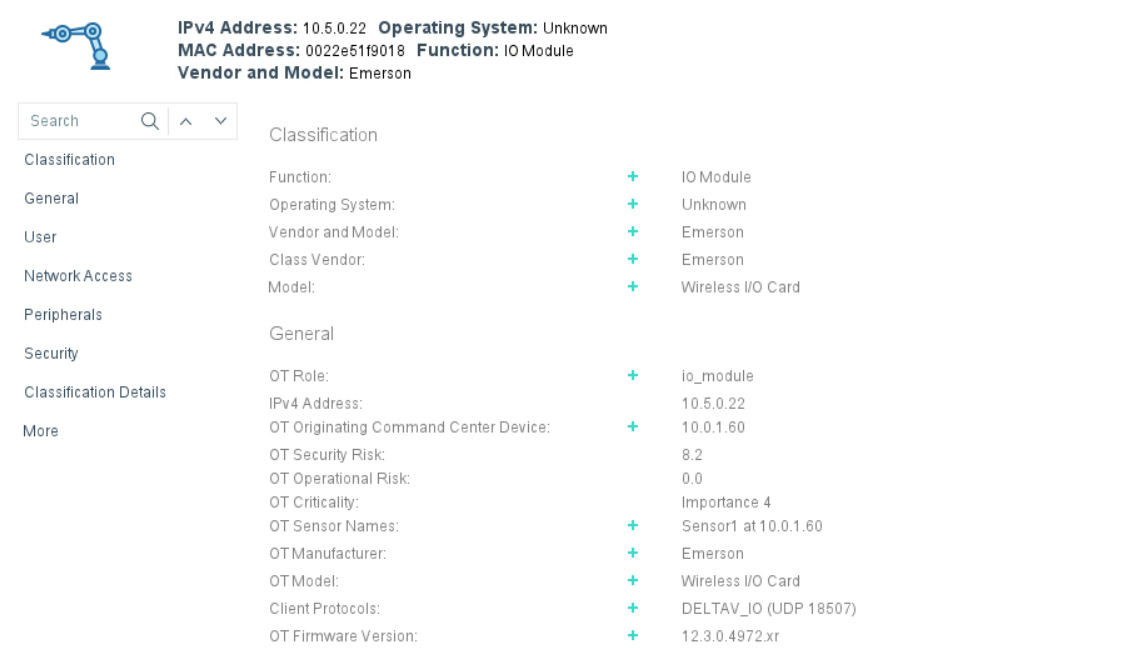
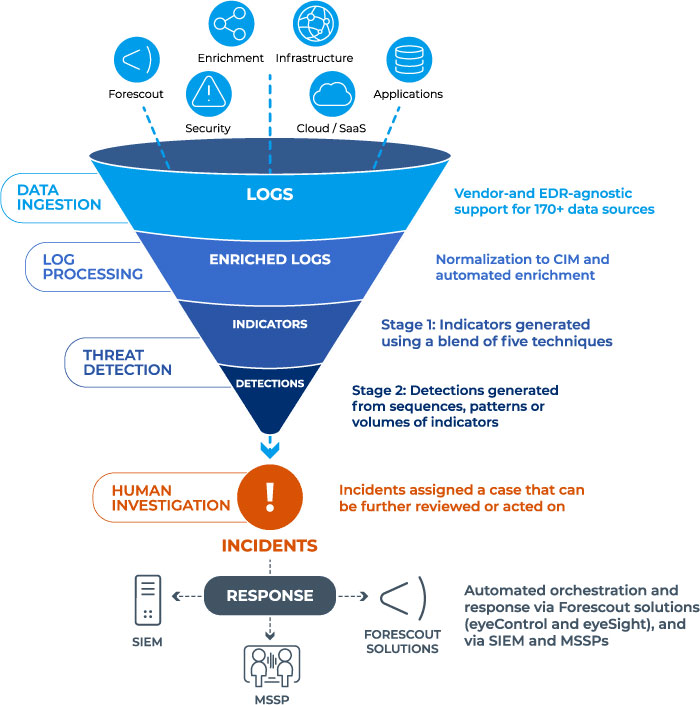
Forescout is a leading provider of cybersecurity solutions, specializing in Zero Trust implementations to secure modern enterprise networks. In today’s dynamic cyber landscape, where traditional perimeter-based security models fall short, Forescout offers a comprehensive approach to Zero Trust security. Forescout’s platform enables agencies to build a rock-solid foundation for Zero Trust by delivering total visibility into connected assets, enforcing least privilege network access and ensuring compliance across multi-vendor environments. By adopting a security design approach based on NIST SP 800-207 standards, Forescout empowers enterprises to achieve Zero Trust without the need for costly infrastructure replacements.
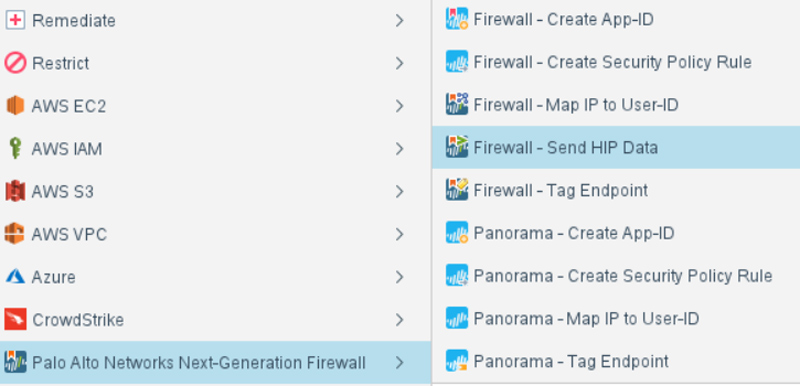
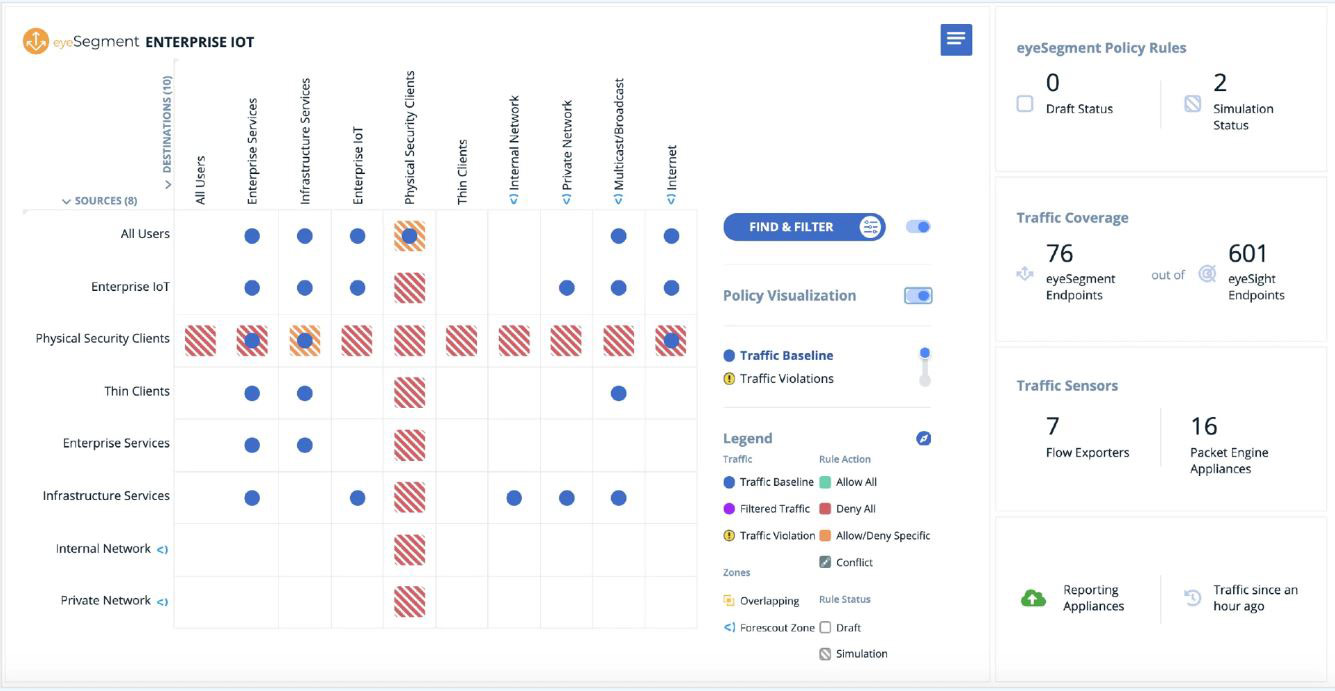
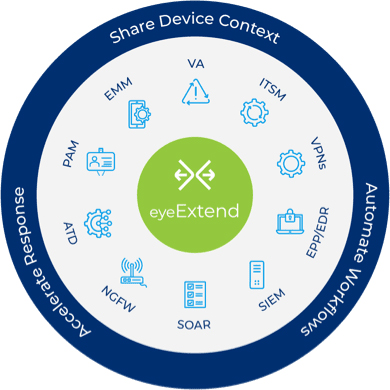
Forescout’s platform is indispensable for agencies embracing the Zero Trust Model. It provides unparalleled visibility into all IP-connected devices across the diverse enterprise segments, including campus, data center, cloud and operational technology (OT) environments. Leveraging integration capabilities with switches, routers and wireless controllers, Forescout enables dynamic network segmentation and real-time threat response. Moreover, Forescout’s platform facilitates seamless collaboration with third-party security and IT management tools, ensuring granular policy enforcement, comprehensive compliance and continuous endpoint control.
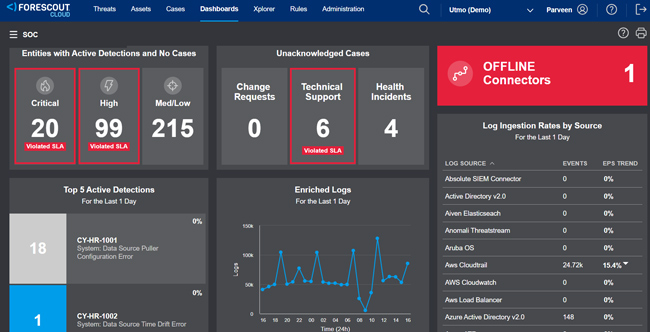
Total visibility is the key
Forescout’s Benefits Snapshot:
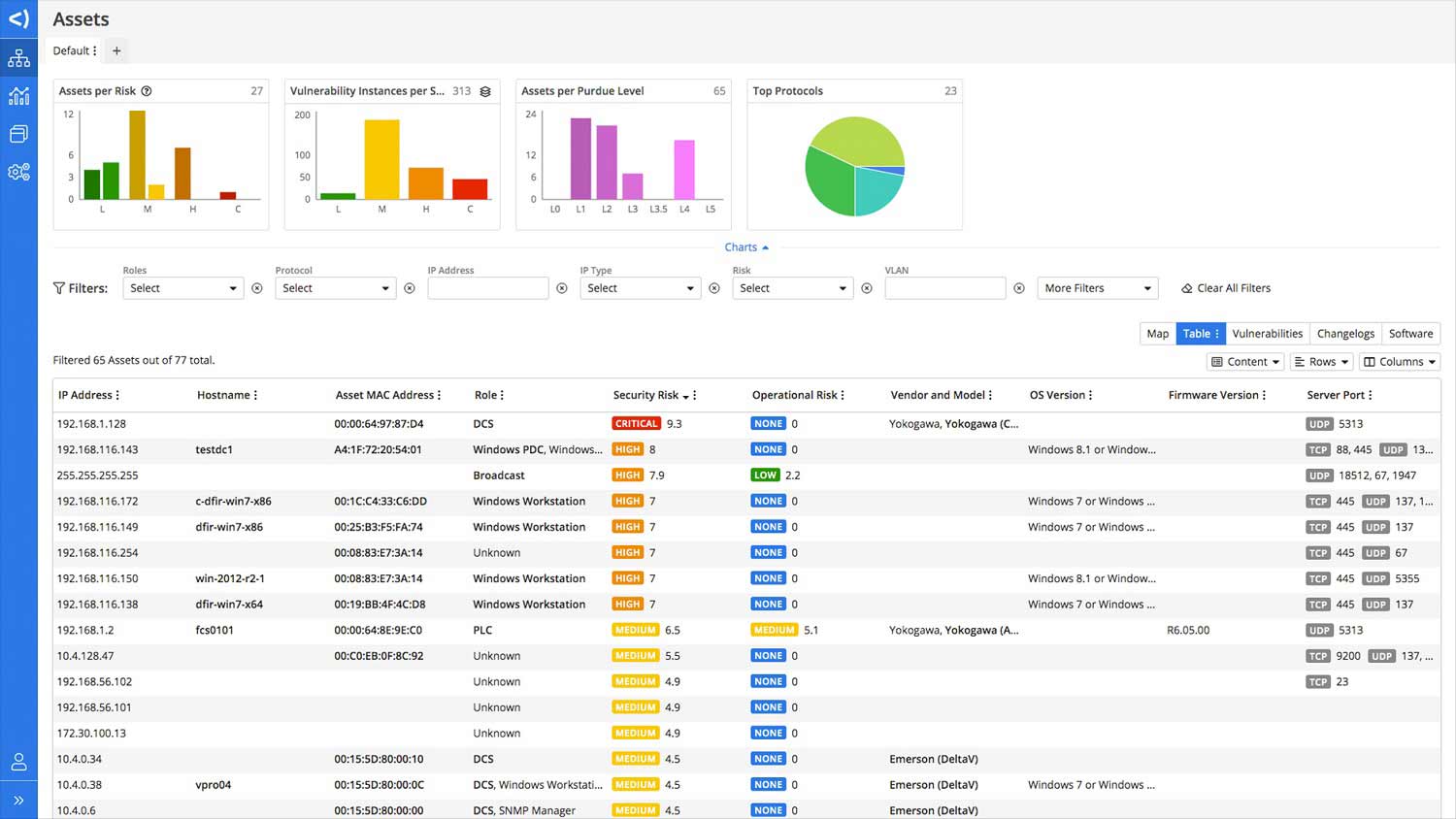
- Total Visibility: Delivers complete visibility into connected assets across enterprise networks, enabling agencies to accurately assess risk and respond to threats effectively.
- Least Privilege Network Access: Enforces least privilege network access, limiting device and user privileges to mitigate attack surface and prevent unauthorized access.
- Compliance and Endpoint Control: Ensures robust compliance adherence, granular policy enforcement and ongoing endpoint control, safeguarding data, devices and infrastructure.