Chainkit FAQ
How does it work?
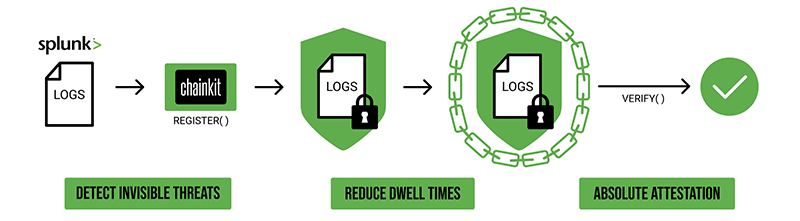
Detect Invisible Threats
Logs are a pillar of modern data processing and Cyber Security. They’re also a prime target of malware, which can make itself invisible by tampering with key log files. Chainkit plugs directly into Splunk to instantly harden your logs.
Reduce Dwell Times
Hardened systems create a Chain of Custody by proactively registering the integrity of their generated logs. During the processing stage, hardened systems verify log integrity to Detect Tampering at the earliest possible moment, before trusting their integrity.
Absolute Attestation
Chainkit takes the digital fingerprints generated by Splunk that users run, and stores them using the Register() API in Chainkit. Later, Splunk can re-run the Chainkit Verify() API to definitively prove whether the data being verified has or has NOT been altered.
What is Chainkit for Splunk?
Chainkit is a post-encryption decentralized service which delivers forensic-class attestation of systems, apps, data and logs at the highest levels of integrity. Chainkit hardens Splunk logs in real-time. We slash detection time from months to minutes.
Chainkit is a Splunk SaaS App, that works with the traditional Splunk Enterprise app as well as the Splunk Enterprise Security app.
How real are cyber threats with Splunk?
Customer surveys are reporting that 39% of cyber security attacks are not detected. The Chainkit solution is focused on detecting this 39% earlier and with absolute attestation. Particularly in the financial services sector, there’s an average of 200 days that these attacks go undetected. With that much dwell time, there is an enormous amount of damage being done by cyber attackers.
Anti-forensics is one of the most common threats to integrity of systems. Once cyber attackers can bypass the encryption on a system, they effectively have the power to now install “device drivers” onto those systems. Those drivers sit beneath the applications and other operating system services, and the tampering happens completely invisibly to apps like Splunk.
Why aren’t encryption and two-factor/ multi-factor authentication enough?
The dark web is a very efficient black market. Your credentials (passwords, etc) are available for sale on dark web marketplaces. There are enough hacks on the dark web that work around two-factor authentication, making these multi-factor authentication credentials no longer an acceptable mitigation of these attacks.
Attackers will purchase or hack Splunk Admin credentials and tamper with your key content. You can have the strongest encryption on the planet, but when a cyber attacker gets your encryption keys through your Admin credentials, encryption can be bypassed.
What are the benefits of using Chainkit for Splunk?
- Mitigate Risk, Tamper Evidence and Reduce Dwell Time
- Chainkit goes above and beyond what traditional encryption can do in a cyber attack. Chainkit can mitigate Splunk-identified risks and get earlier detection closer to real-time. Chainkit also provides tamper evidence for indicators of compromise that fulfills requirements set by many companies to help reduce dwell time and contain these attacks.
- Detect Data Poisoning
- Chainkit also works with Splunk AI extensions to attest machine learning integrity and detect adversarial AI, or “data poisoning”. One of the key ways of attesting to machine learning integrity is to prove the integrity of the data sets used for training and the inference/input stream. Chainkit provides reproducibility and achieves compliance through absolute attestation.
- Full Integrity of Forensic Artifacts
- Chainkit provides full integrity of forensic artifacts. Our solution provides closure to damaging attacks automatically by default. Inconclusive data is very dangerous because adversaries can easily exploit you again. It’s very important for forensic investigators to get full integrity of those forensic artifacts to quantify and mitigate risk.
- Lower Cyber Insurance Premiums
- You can easily tweak your configuration settings with Chainkit for Splunk to gain any kind of granularity or cadence that you want. Chainkit effectively brings a lot of the forensic work upfront as opposed to after the attack. This will dramatically lower cyber insurance premiums by giving you the ability to show an underwriter that you have full attestation and tamper evidence for indicators, and full integrity for forensic artifacts.
Who can benefit from using Chainkit for Splunk?
Chainkit for Splunk target users include:
- Cyber Security - Security Operations, Detection & Response, Security Analysts, Threat Hunters
- DFIR - Digital Forensics & Incident Response
- Compliance - Security Policy, Infrastructure (ISO, etc), Data
- Audit

