Security Control Management for IT Infrastructure
Continuous Hardening, Across Every Deployment
Inside American defense and intelligence agencies, security and compliance for IT infrastructure is slow, manual, and fragmented. Misconfigurations and missed patches leave the door open to attacks, while disjointed authorization processes take months and cost millions, only to leave systems outdated upon delivery.
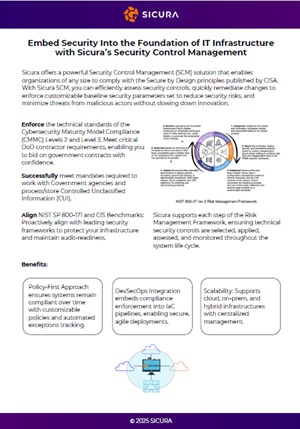
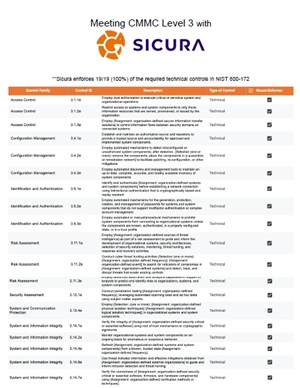
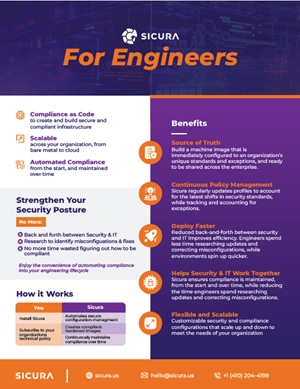
Security Control Management (SCM) provides a paradigm shift to continuous hardening, across every deployment. SCM solutions automate assessment, enforcement, and validation, while integrating with commonly-used engineering and compliance workflows. Developed at NSA, SCM is purpose-built for national security.
Operationalize Next-Generation Compliance Frameworks with Sicura
Sicura’s Security Control Management (SCM) directly aligns with the DoD’s CSRM-C and cATO initiatives by automating continuous control enforcement and evidence generation. Maintain authorization while meeting the speed and rigor these new frameworks demand.
"Sicura's SCM solution gives us full visibility and control over our entire infrastructure. We can continuously monitor configurations, detect deviations in real time, and ensure that every system remains secure and compliant. It has become an essential part of our cybersecurity operations."
- Mark Fitch, Army DevCom C5ISR
Led by a team with decades of experience in the NSA and DoD. Backed by leading investors, including Squadra Ventures, Scout Ventures and Blue Wing Capital.