Explore Venafi's Self-Guided Tours
Venafi and Carahsoft have partnered together to provide a series of self-guided tours of Venafi's products and features. Similar to a live demo, the self-guided tours explores how Venafi's products and features applies to a specific technology vertical such as Cybersecurity.
Learn about Venafi's benefits, watch a short pre-recorded demo video, and download related resources. If interested in furthering the conversation, you can also schedule a live demo with a Venafi expert from Carahsoft. Start a Self-Guided Tour now by selecting one below:
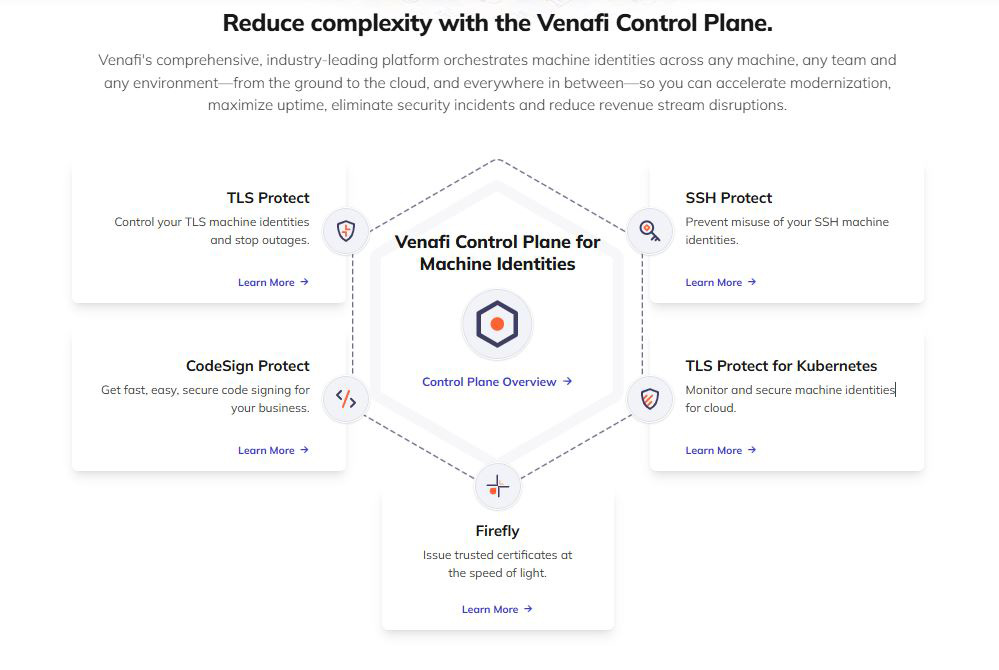
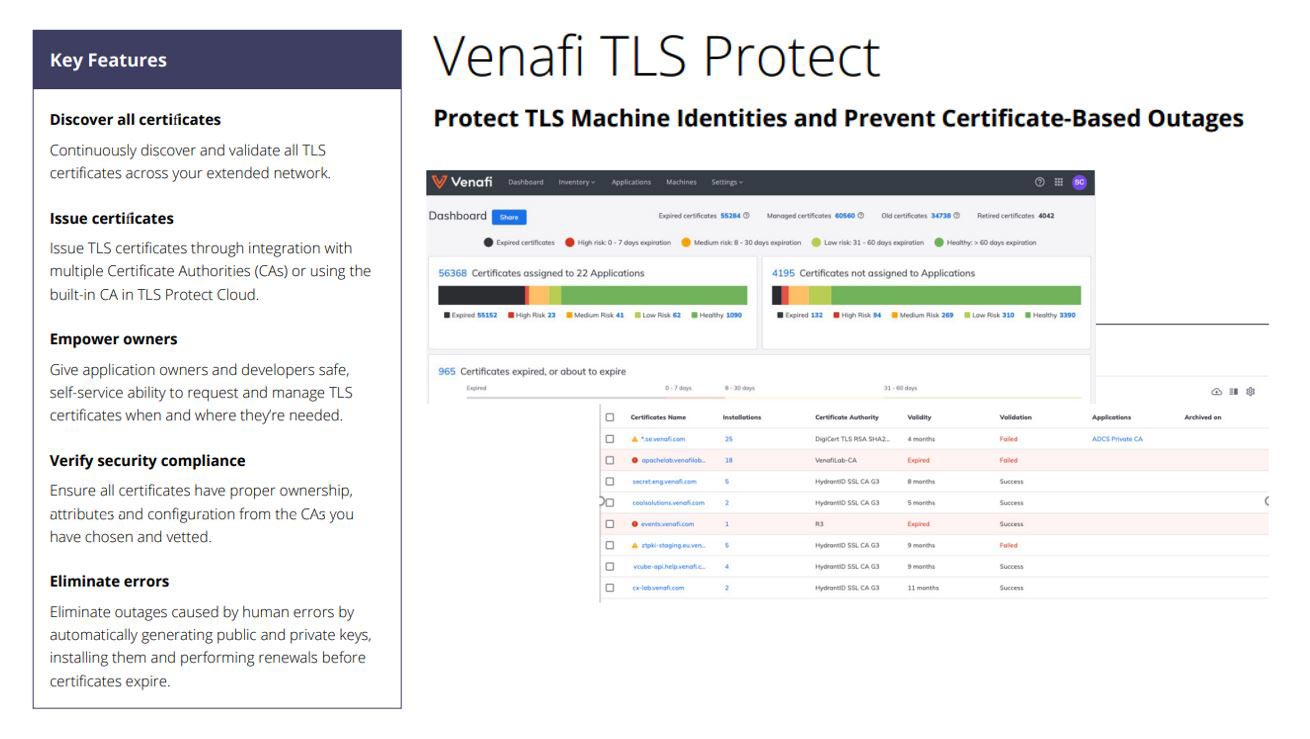
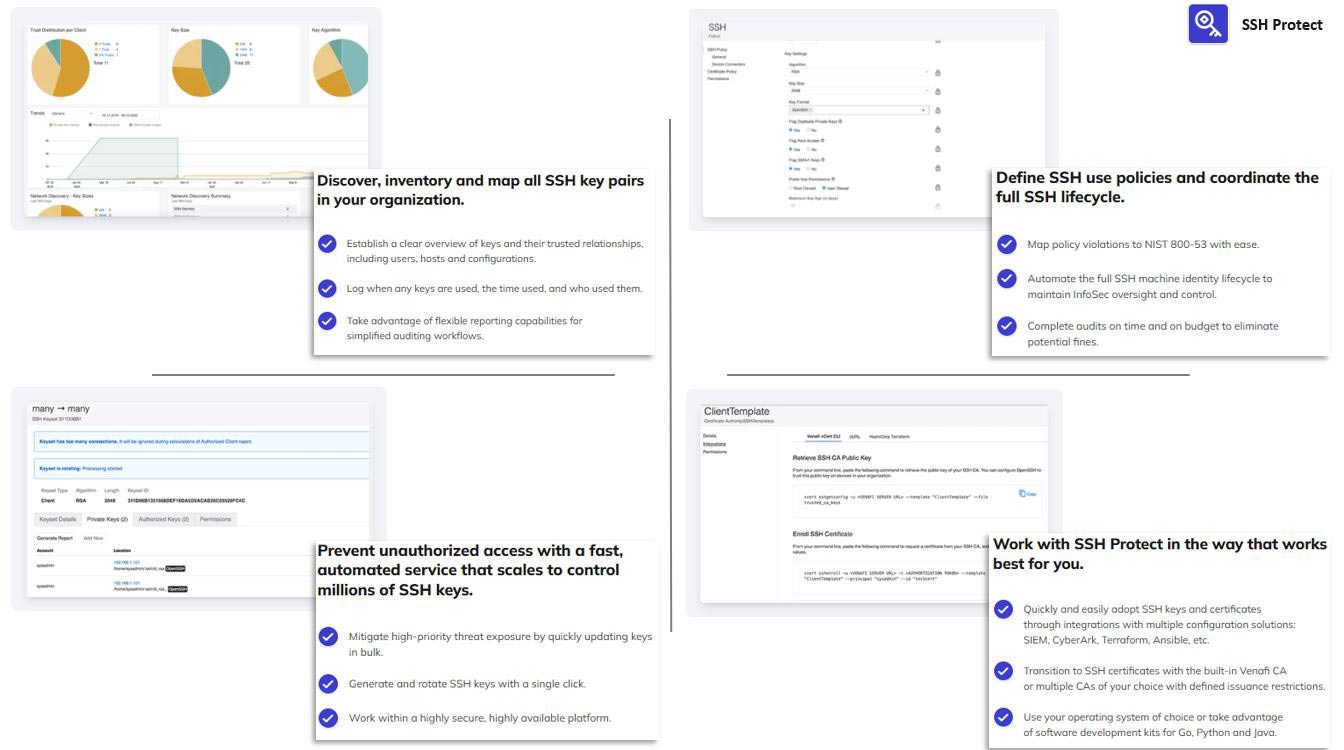
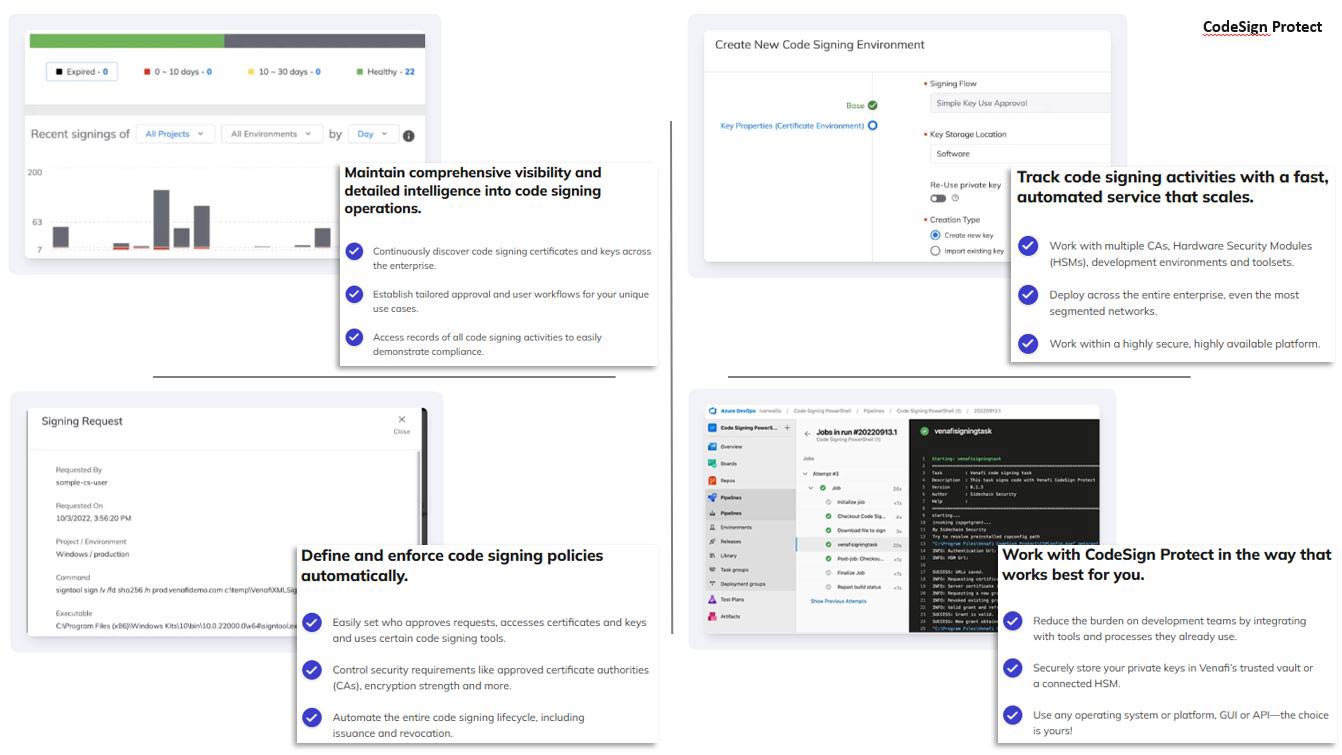
Venafi delivers cutting-edge data security by orchestrating machine identities across modern, cloud-native and microservice-based environments. As traditional perimeters dissolve, the explosion of machine identities and the complexity of managing them pose significant challenges. Venafi’s industry-leading platform simplifies this by securing and managing cryptographic keys and digital certificates across any machine, team or environment—from on-premises to the cloud. This ensures secure and private machine communications, accelerates modernization efforts, maximizes uptime and minimizes security incidents and revenue disruptions. Trusted by public agencies and enterprises alike, Venafi enables seamless management of the entire machine identity lifecycle to protect today’s dynamic IT landscape.
Want to learn more about Venafi?
Start a self-guided demo now to learn more about data security and machine identity management.
Venafi's Benefits Snapshot:
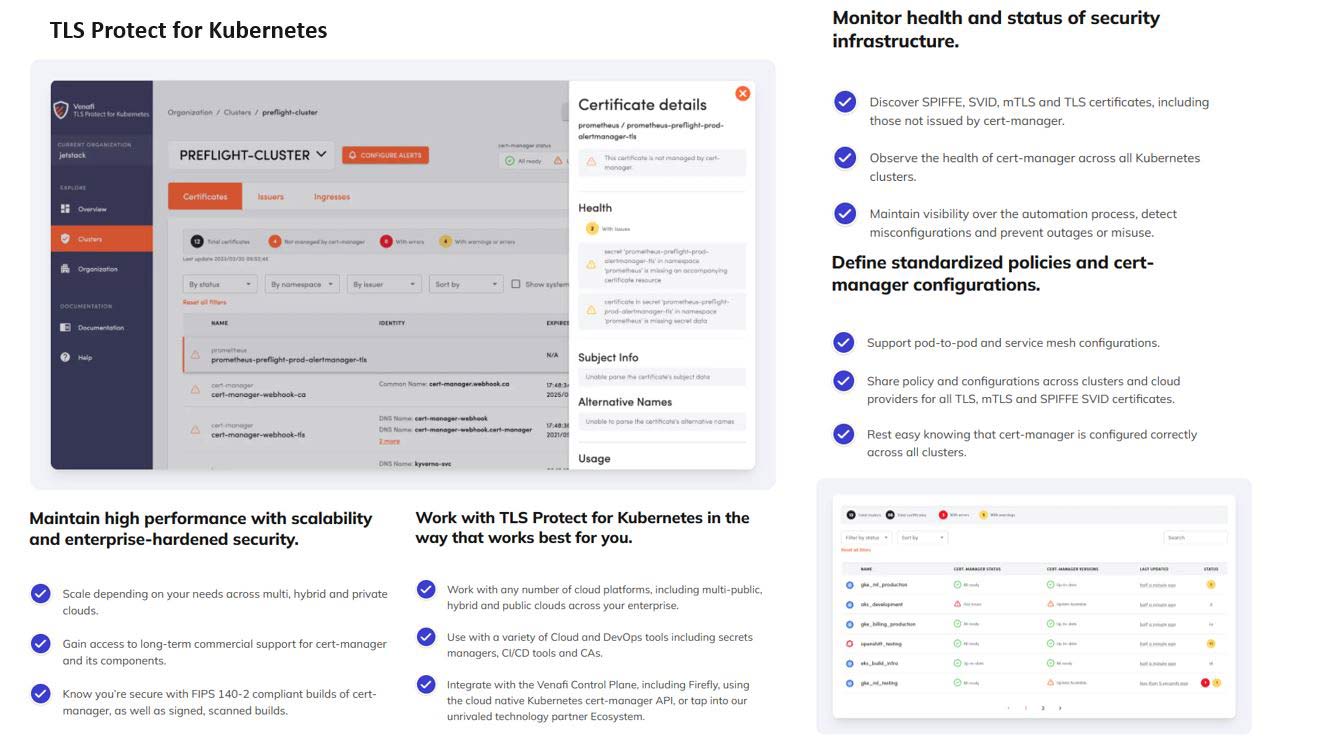
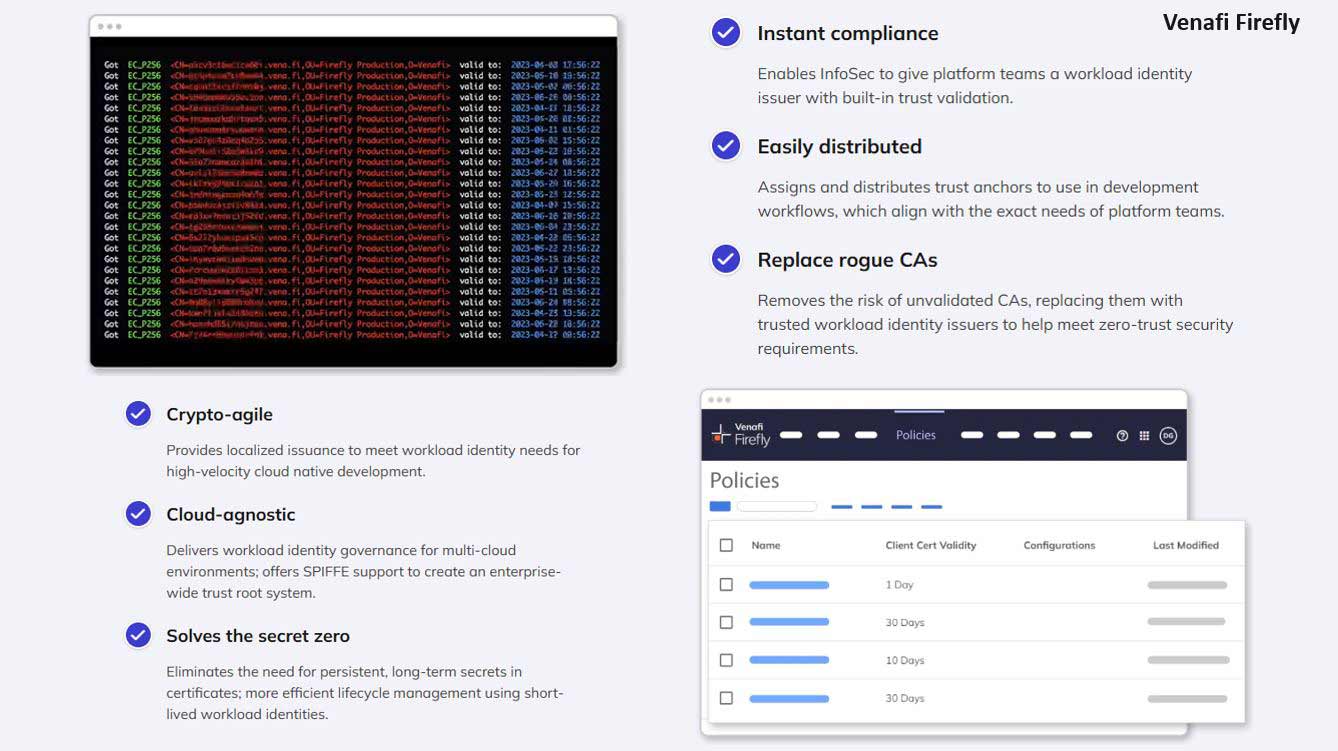
- Strengthens security with continuous risk identification and mitigation
- Eliminates certificate-related outages with certificate lifecycle automation
- Improves governance with enhanced audit responsiveness