Explore Trellix's Self-Guided Tours
Trellix and Carahsoft have partnered together to provide a series of self-guided tours of Trellix's products and features. Similar to a live demo, the self-guided tours explores how Trellix's products and features applies to a specific technology vertical such as Zero Trust and Cybersecurity.
Learn about Trellix's benefits, watch a short pre-recorded demo video, and download related resources. If interested in furthering the conversation, you can also schedule a live demo with a Trellix expert from Carahsoft. Start a Self-Guided Tour now by selecting one below:
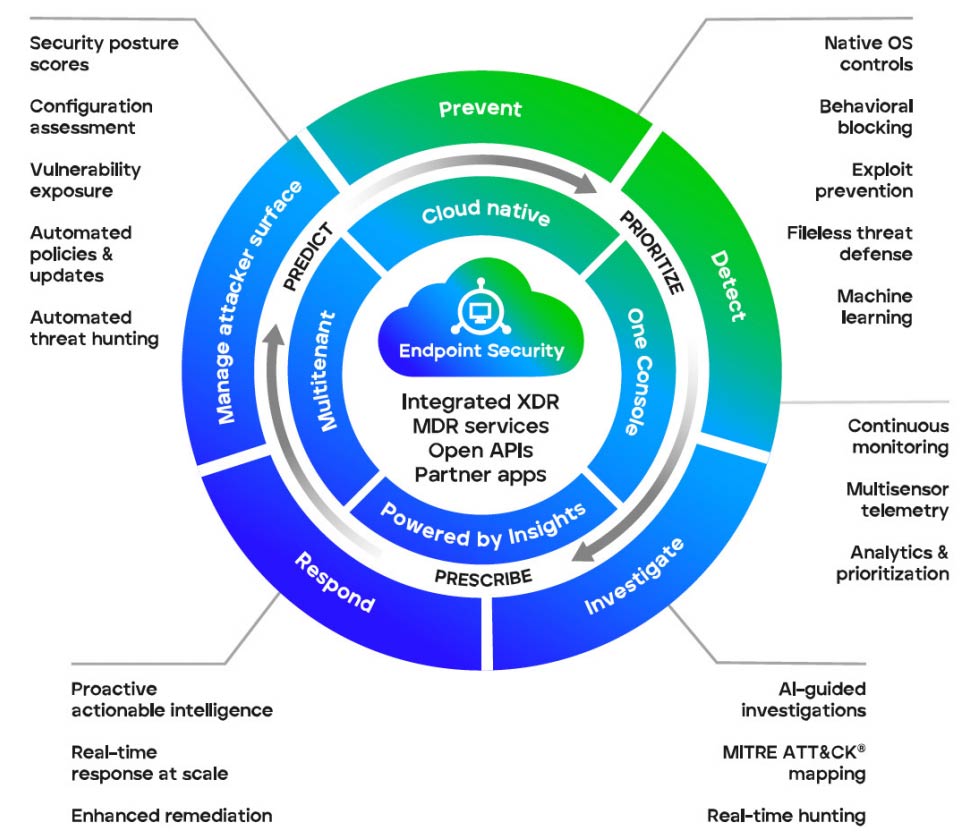
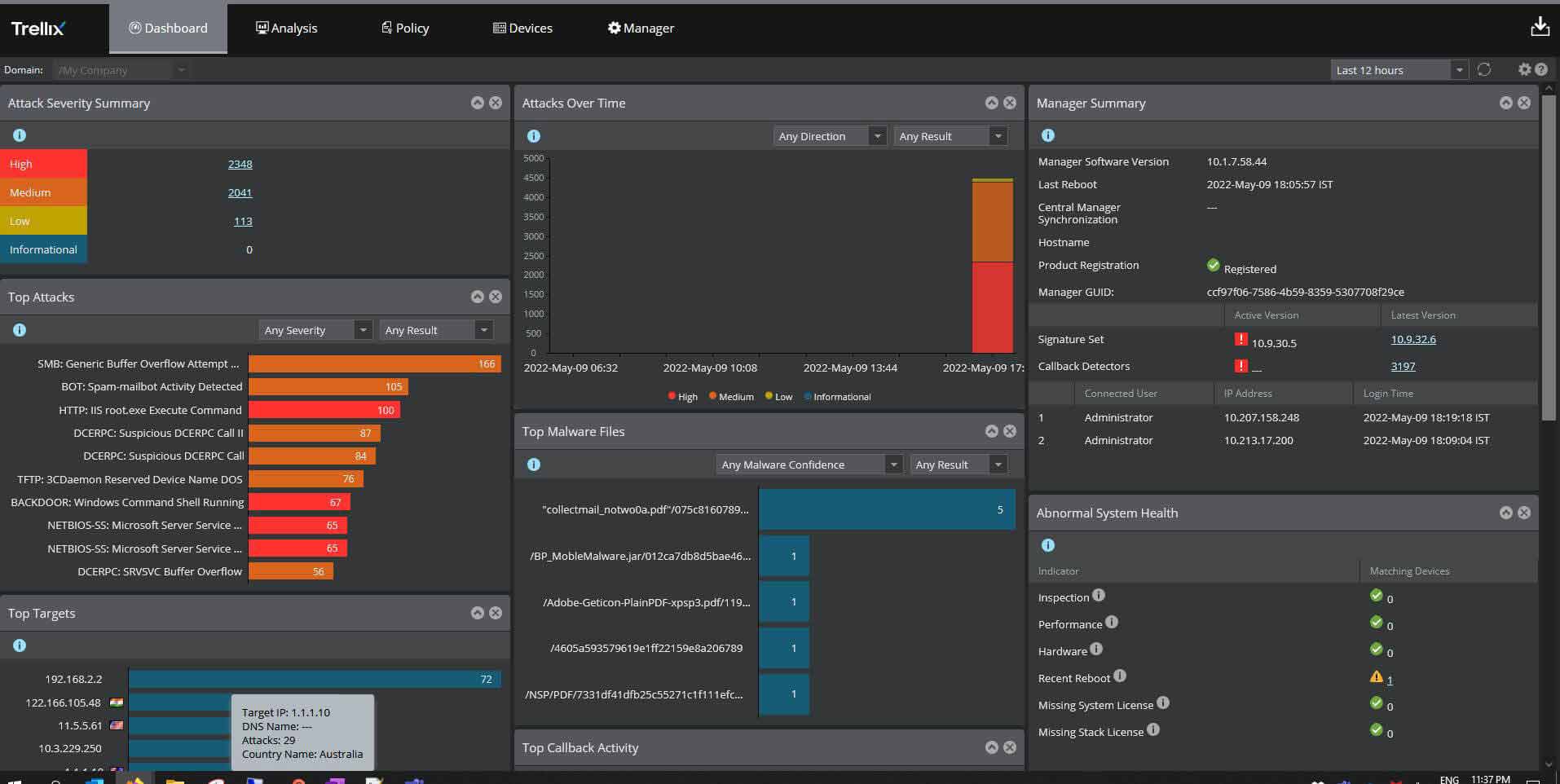
Trellix offers comprehensive Endpoint Security (ENS) solutions designed to protect and empower Government agencies’ workforces in today’s evolving threat landscape. With Trellix integrated security framework, every endpoint is safeguarded through proactive threat intelligence and defenses, ensuring heightened resilience against cyber threats. Through proactive and intelligent endpoint protection and Extended Detection and Response capabilities, Trellix equips agencies with actionable intelligence, machine learning and advanced technologies to continuously monitor threats and thwart attacks effectively.
Want to learn more about Trellix?
Start a self-guided demo now to learn more about Trellix’s suite of endpoint protection technologies.
Trellix's Benefits Snapshot:
- Offers dynamic protection against advanced threats, continuously adapting to secure your agency. Benefit from robust threat protection, detection, investigation and response capabilities for proactive defense and comprehensive endpoint control.
- Simplify security management with Trellix Endpoint Security’s centralized console, scaling effortlessly across numerous endpoints. Access automated workflows from anywhere, prioritize tasks efficiently and streamline operations for time-saving management.
- Stay ahead of adversaries with proactive risk management features, including threat prioritization and preemptive prevention. Gain actionable insights quickly, predict potential security gaps and assess your agency’s readiness against attack scenarios.
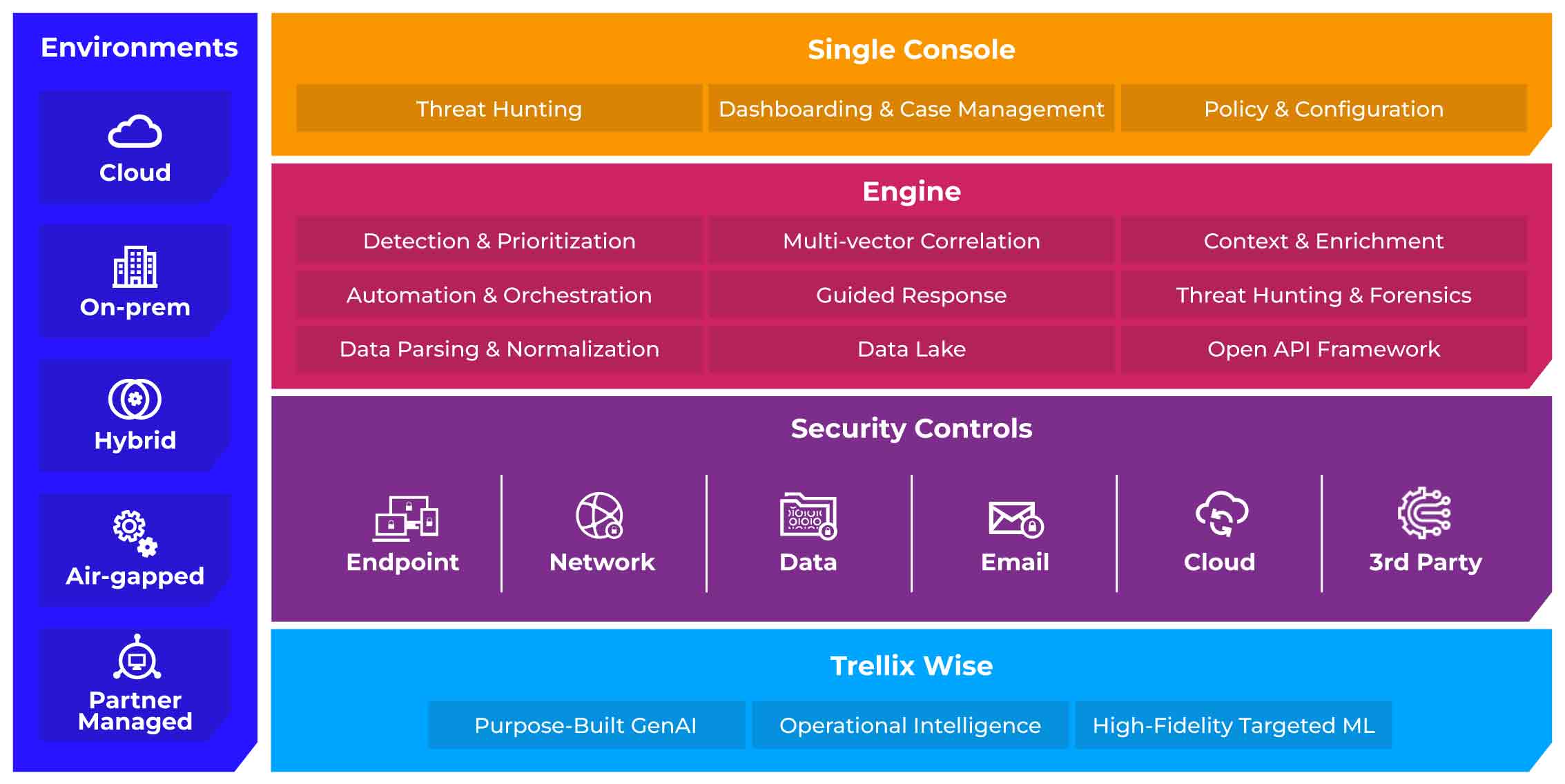
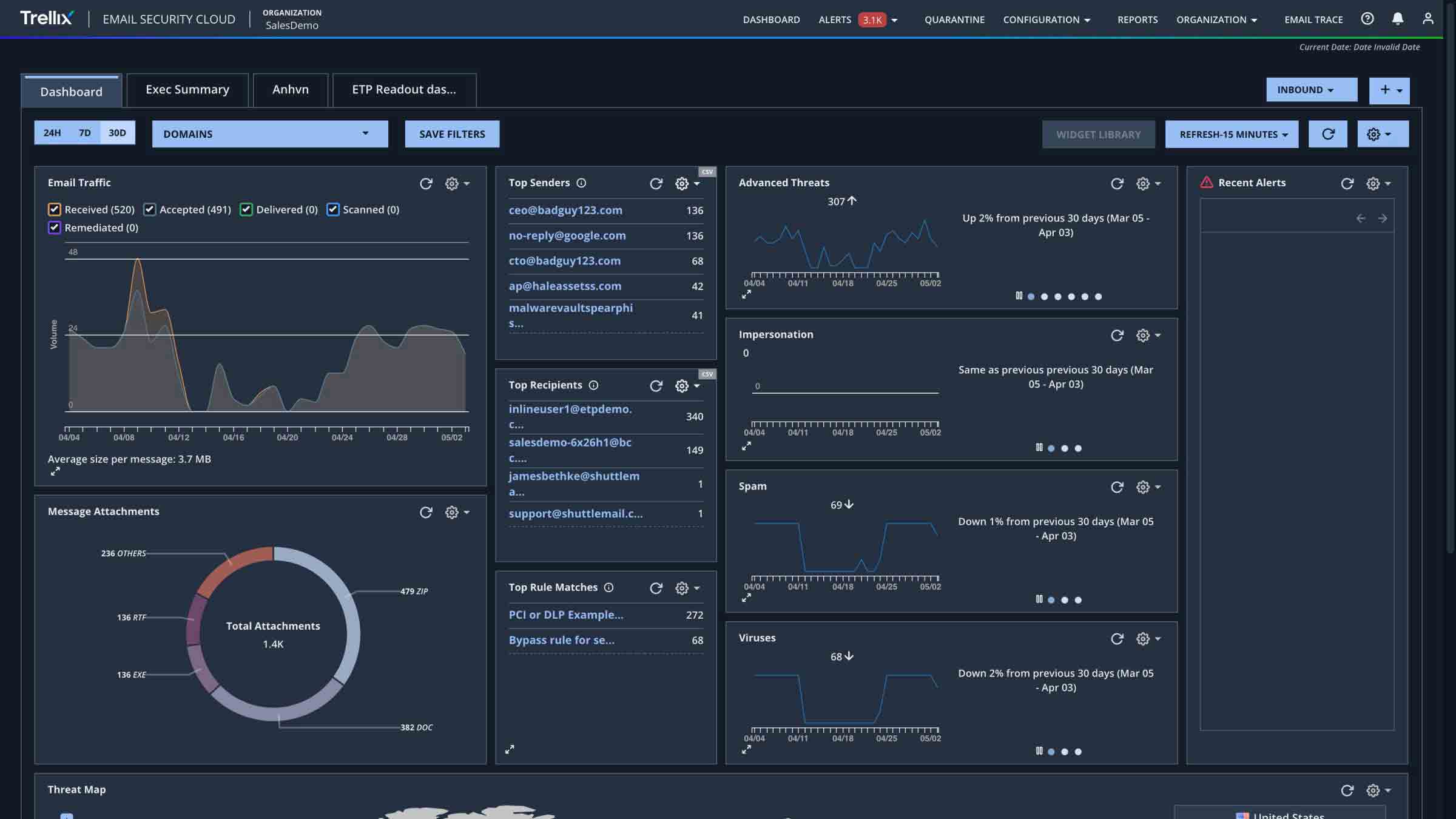
Trellix is at the forefront of cybersecurity, offering an AI-powered Extended Detection and Response platform designed to strengthen Zero Trust strategies. Implementing a Zero Trust approach requires comprehensive visibility across endpoints, network traffic, cloud security and data security—areas where Trellix excels with unparalleled visibility through its platform, integrating native security controls and third-party solutions.
Trellix is empowering agencies with innovative solutions, leveraging machine learning and automation to deliver proactive, resilient cybersecurity that instills confidence in operational security and protection.
Want to learn more about Trellix?
Start a self-guided demo now to learn more about how Trellix’s AI-powered platform can enhance your Zero Trust strategy.
Trellix's Benefits Snapshot:
- Improves Zero Trust frameworks by correlating data from multiple sources, providing multi-vector correlation to increase visibility and security against advanced attacks.
- Eliminates blind spots with rapid data ingestion and centralized SecOps management, reducing mean time to detect (MTTD), investigate (MTTI) and respond (MTTR) through ML-guided investigations and automated responses.
- Streamlines security environments by consolidating with native security controls, reducing alert fatigue and simplifying management while integrating with leading Identity Access Management providers to contextualize insider threats and credential-based risks.