ShardSecure Solutions for the Public Sector
-
Agentless file-level protection
In the past, organizations protected their data from unauthorized access with agent-based encryption solutions. Unfortunately, traditional agent-based solutions tend to slow performance by 5% to 40%. They are also difficult to manage and scale and may be incompatible with newer workloads and cloud services.

ShardSecure offers an innovative, agentless alternative to agent-based file-level protection with “set and forget” management. The ShardSecure platform secures data from threats without the cost and complexity of agent-based solutions and provides strong data confidentiality and resilience in the process.
ShardSecure’s API-based abstraction layer sits between applications and storage infrastructure, where it performs advanced file protection. This approach allows for an easy plug-and-play implementation without changes to data or user workflows.
ShardSecure’s low latency and fast throughput architecture have minimal to no performance impact. Data on end devices can be accessed without requiring changes to existing applications.
-
Meeting regulatory requirements for data privacy
A growing number of jurisdictional data privacy regulations make it difficult for businesses to store data where they want. With strict cross-border data privacy laws like the EU’s General Data Protection Regulation (GDPR), the anticipated Schrems III ruling, and CCPA/CPRA in the US, it’s becoming increasingly difficult for companies to protect their data, remain compliant, and take advantage of the cloud.
With ShardSecure, you can use the cloud storage providers of your choice, in the geographic locations and jurisdictions of your choice, to mitigate data transfer risk and address data sovereignty and compliance concerns. Data can be distributed across different regions of a single cloud provider, across multiple cloud providers, or across a hybrid mix of on- premises storage and one or more cloud providers.
ShardSecure also meets the requirements of the EDPB’s Use Case 5 in Schrems II. The ShardSecure platform is a split processing technology that can be easily deployed in a multi- party processing environment, meaning that it allows organizations to store and process data safely under Use Case 5.
As cyber audit and assurance firm UHY Advisors states: “ShardSecure has the potential to lower cyber risks and compliance costs while maintaining compliance with the spirit of European and US data protection regulations.”
-
Robust data resilience
Accidental misconfigurations, extreme weather, and cyberattacks can cause companies to lose access to their most important data. ShardSecure mitigates these risks by keeping data available, accessible, and accurate in the face of tampering, deletion, outages, ransomware, and other unexpected events.
The ShardSecure platform maintains high availability at multiple levels. Each instance of ShardSecure is a virtual cluster that can be run on-prem or in the cloud, and customers can configure two or more virtual clusters for failover.
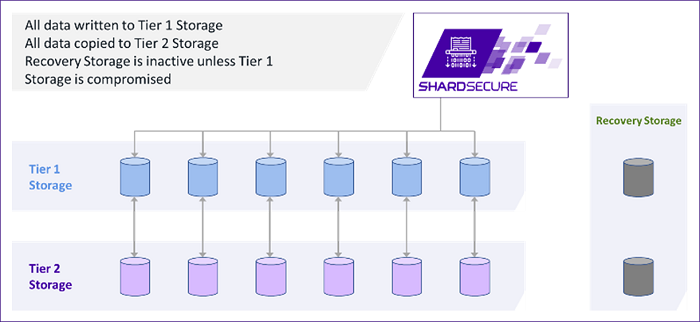
ShardSecure’s configurable data migration feature allows admins to automatically migrate data to a safe alternate location in the event that tampering is detected. If a specified number of data integrity check failures take place, all the data in the affected storage location can be automatically migrated to the secure location with no downtime.
-
Mitigate ransomware risks
ShardSecure offers transparent, real-time reconstruction of data that has been encrypted by ransomware. As soon as data fails a data integrity check, the ShardSecure platform automatically reconstructs affected data to minimize downtime and prevent disruption to users and data flows.
ShardSecure maintains strong data integrity with multiple health checks to detect unauthorized data tampering, alert security teams of a potential attack, and automatically reconstruct compromised data in real-time. This ensures that data remains accurate and unaltered, not just available.
The ShardSecure platform also mitigates the impact of double extortion ransomware attacks, where criminals threaten to release or sell sensitive data that they have exfiltrated prior to encrypting it. Since the ShardSecure platform renders data unintelligible to unauthorized users, exfiltrated data is of no value to attackers.
-
Protection for AI/ML models & training data
Given their importance, cost, and susceptibility to tampering, protecting AI/ML models and training data is becoming a priority for organizations. AI/ML models and training data are typically stored in the cloud with providers like AWS, Azure, and GCP, which can present unique data privacy risks. Cloud admin access to sensitive data means that companies must take additional security measures to keep these high-value models and datasets safe.

ShardSecure protects AI/ML models and training data in the cloud and in multi-cloud architectures. The platform prevents unauthorized access to data, allowing organizations to safeguard their AI and ML datasets without the complexities and overhead of traditional security solutions. With advanced data security, support for data sovereignty, robust data resilience, and simple integration, ShardSecure mitigates common threats to AI/ML models and training data integrity, such as exposure and tampering.
-
Additional use cases
Beyond the benefits listed above, ShardSecure also:
- Protects sensitive files so teams can collaborate safely and without losing functionality.
- Integrates with existing cloud backup solutions to further protect backup data.
- Accelerates cloud migration and transformation initiatives.
- Supports secure cold storage migration from on- prem to the cloud.

