Network Visibility and Security Posture Validation for the Age of AI
Government agencies need the ultimate network visibility to build, scale, and protect vital digital assets and operations—especially as AI changes everything. Keysight solutions for visibility and validation equip network administrators, security teams, and developers with vital real-time insights into users, applications, devices—and threats—everywhere in their hybrid environments.
Modernization takes the right Vision
Keysight’s network visibility platform provides a future-ready foundation for ongoing digital transformation and Zero Trust cybersecurity. Only Keysight brings:
The industry’s widest selection of taps to capture packet data from any network, data center, OT or IoT environment, and private or public cloud to detect and deflect threats, optimize monitoring and performance, and reduce cost.
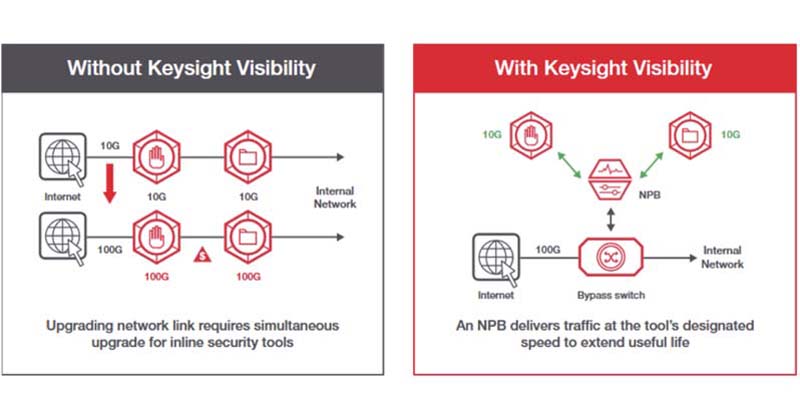
Bypass switches that ensure fail-safe resilience for inline security and out-of-band performance monitoring.

Security takes constant validation
Monitoring for threats can never be a ‘one and done.’ Keysight’s test and network simulation tools validate performance against KPIs (throughput, latency, jitter, loss, quality of service) and evaluate complex security postures. Combine visibility and cyber defense validation to avoid risk from ransomware, encrypted threats, and outages caused by link or device failure.
We’ll answer your key questions—and more
Keysight solutions help government IT and security teams get the answers they need:
- Can your firewalls detect AI-led threats, even during peak loads or DDoS attacks?
- Is your SIEM receiving reliable alerts?
- How much latency can your satellite-based applications withstand?
- Can you monitor Critical Infrastructure (CI) assets reliably, even in harsh conditions?
- Are tool investments achieving their full ROI? Can you improve utilization?
Why Keysight?
With 20 years’ experience serving the public sector, we bring the experience, technology solutions, and world-class support government agencies need to modernize, defend, and deliver a world-class user experience (UX).