Global Cybersecurity Best Practices Community
The Center for Internet Security® (CIS®) makes the connected world a safer place for people, businesses, and governments through our core competencies of collaboration and innovation. CIS is a community-driven nonprofit, responsible for the CIS Critical Security Controls® and CIS Benchmarks®, globally recognized best practices for securing IT systems and data. CIS leads a global community of IT professionals to continuously evolve these standards and provide products and services to proactively safeguard against emerging threats.
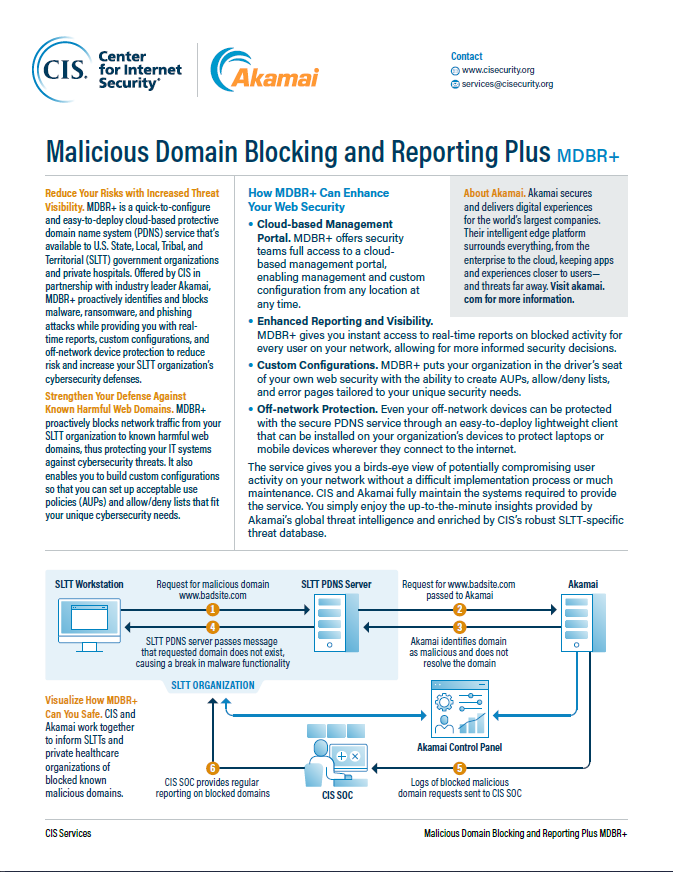
CIS Hardened Images® provide secure, on-demand, scalable computing environments in the cloud. CIS is home to the Multi-State Information Sharing and Analysis Center® (MS-ISAC®), the trusted resource for cyber threat prevention, protection, response, and recovery for U.S. State, Local, Tribal, and Territorial government entities.

Hardened Images provides users with a secure, on-demand, and scalable computing environment. Available now on AWS Marketplace, Azure, Google Cloud, and more.
Learn More ->

Secure your organization with resources and tools designed to harness the power of CIS Benchmarks and CIS Controls.
Learn More ->

MS-ISAC® Membership offers SLTT organizations a trusted community with tailored cybersecurity services, threat intelligence, 24x7x365 SOC support, and collaborative resources designed to fit any size or budget.
Learn More ->