The shift to Atlassian Government Cloud unlocks new potential for federal agencies
Modernization has been a Federal priority for over a decade, but the realities of legacy systems, compliance mandates and limited resources have forced IT leaders to make hard tradeoffs. The pandemic accelerated digital transformation, proving just how critical resilient, cloud-based systems are to mission continuity and citizen services.
Yet many agencies have remained tethered to on-premises tools not by choice, but by compliance constraints.
Now that Atlassian Government Cloud is FedRAMP Moderate authorized, agencies can confidently shift core collaboration and service delivery workloads to the cloud with security and compliance in place.
The opportunity to modernize is clearer than ever. With compliance barriers removed, cloud adoption becomes not just feasible, but foundational to moving missions forward.
FedRAMP Moderate removes the guesswork
Atlassian Government Cloud is a dedicated environment built specifically for public sector teams and limited to U.S. Government agency and contractor usage. It delivers the performance Federal agencies need, with the security and compliance they require.
This includes:
- FedRAMP Moderate Authorization for Jira, Confluence and Jira Service Management
- Dual-region hosting on AWS commercial US East/West regions
- Continuous monitoring aligned to FedRAMP Moderate standards
Atlassian’s Government cloud platform is built on the same architecture that powers Cloud Enterprise, offering the scale, reliability and control public sector teams need. It’s designed to reduce friction and deliver continuous innovation while maintaining trust and transparency.
From patching systems to powering missions
Agencies that remain on legacy infrastructure are fighting a battle on two fronts: maintaining outdated systems while trying to meet new mission demands. That approach is no longer sustainable.
Modernizing with Atlassian Government Cloud eliminates the distractions of infrastructure maintenance and opens the door to high-impact work. Instead of managing update cycles or responding to fire drills, IT teams can shift their focus to scaling digital services, working with disparate teams and improving citizen-facing outcomes.
For IT administrators, this shift is transformational. Cloud offloads the operational burden they’ve carried for years—manual upgrades, weekend patching, surprise outages. With that weight lifted, teams can focus on enabling smarter service delivery across the agency.
As Jeff Garrett, Technical Product Manager at the California Department of Health Care Services shared, “I’ve had to maintain server infrastructure in the past. It’s not pleasant. Being on Atlassian Cloud Enterprise means we don’t have to do that anymore. Plus, we can add and remove applications quickly.”
This is how mission work moves forward with greater speed, clarity and alignment.
Built-in collaboration, automation, and insight
Atlassian Government Cloud offers more than security and compliance. It enables new ways of working across teams and departments, aligning your entire agency and harnessing your data.
Consider this scenario: A Federal program team launches a new initiative to expand community outreach. Rather than waiting weeks for a custom workflow, they spin up a new Jira project using a pre-built template with no administrator required. HR and legal teams contribute to project planning in Confluence, while real-time insights track progress across departments. No tickets. No silos. Just forward momentum.
The scenario above shows how teams can move faster using features like team-managed projects and templates in Jira, along with native incident management in Jira Service Management.
In addition to streamlining work, Atlassian Government Cloud will soon include Atlassian Analytics, bringing cross-product visibility and supporting data-driven decision-making across teams.
Beyond what’s available in Atlassian Government Cloud today, we’re also committed to delivering the same innovative features you’ll find in our commercial products, like Confluence Whiteboards and Goals. We’re actively developing our roadmap for Atlassian Government Cloud and will share more information soon.
Migration isn’t a barrier. It’s a supported journey
Atlassian has helped thousands of organizations transition to the cloud, including some of the world’s largest enterprises and Government agencies. We have reliable tooling for migrating data from Data Center to Atlassian Government Cloud that has been hardened through years of supporting migrations to commercial cloud. And for those migrating from commercial cloud to AGC, we’re releasing tooling for this soon.
Federal teams benefit from specialized migration support designed to streamline the process and minimize risk. That includes:
- A Cloud Migration Manager assigned to each Atlassian Government Cloud project
- Migration guides, training resources and toolkits to support end-user adoption
- The choice to engage with a network of experienced solution partners if your agency wants even more support.
Agencies already using Atlassian Cloud are seeing measurable results that support faster delivery, smarter governance and stronger collaboration:
- Utah Department of Technology Services cut Jira project setup time by 90%, enabling faster response to internal and citizen needs
- California Department of Health Care Services standardized on Atlassian Cloud and reduced one project’s delivery time from 18 months to 6 months, cutting costs from $2.8M to $600K
With Atlassian, cloud migration becomes a guided path to modernization — not an obstacle.
The results are measurable
The shift to Atlassian Government Cloud delivers tangible results. Early adopters, including public sector agencies and private sector enterprises, are already seeing gains in performance, collaboration, and insight.
In a recent customer impact survey, organizations migrating to Atlassian Cloud reported:
- Up to a 53% increase in productivity
- 47% improvement in cross-functional collaboration
- 44% gain in insight-driven decision-making
These outcomes directly support the goals of Federal agencies: improved cross-team collaboration, greater agility and faster progress on mission priorities. In a time when agencies are under pressure to do more with less, results like these make a big impact.
Take the next step
With FedRAMP Moderate authorization in place, Federal agencies can now adopt Atlassian Government Cloud with confidence. It’s time to move from maintaining systems to empowering missions.
Curious about your agency’s migration path to Atlassian Government Cloud? You can become a part of our Early Access Program. Join the waitlist here!
Carahsoft Technology Corp. is The Trusted Government IT Solutions Provider, supporting Public Sector organizations across Federal, State and Local Government agencies and Education and Healthcare markets. As the Master Government Aggregator for our vendor partners, including Atlassian we deliver solutions for Geospatial, Cybersecurity, MultiCloud, DevSecOps, Artificial Intelligence, Customer Experience and Engagement, Open Source and more. Working with resellers, systems integrators and consultants, our sales and marketing teams provide industry leading IT products, services and training through hundreds of contract vehicles. Explore the Carahsoft Blog to learn more about the latest trends in Government technology markets and solutions, as well as Carahsoft’s ecosystem of partner thought-leaders.












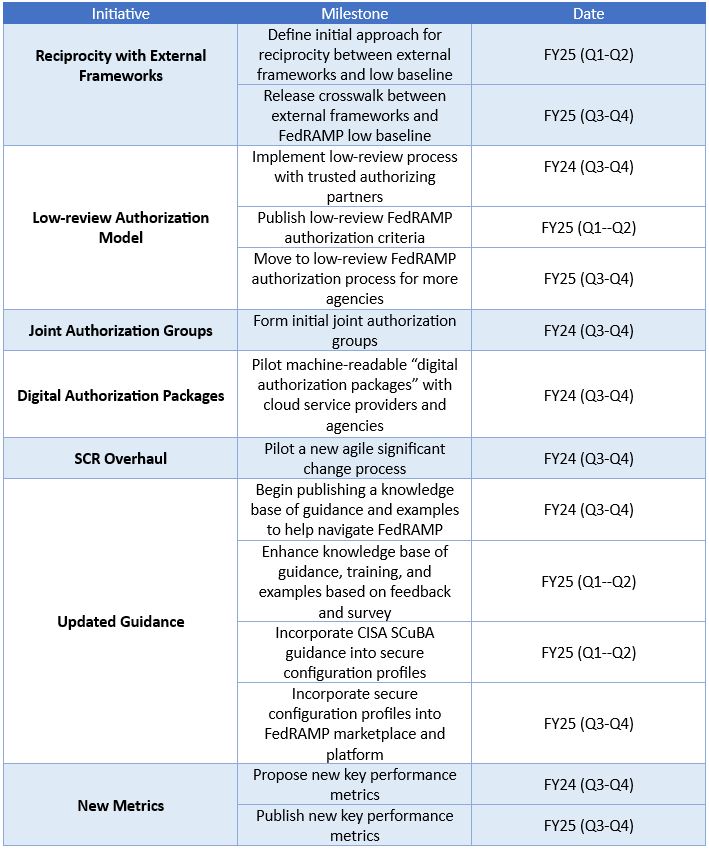
 Automation and Continuous Monitoring (ConMon) stand at the forefront of FedRAMP modernization as the memo underscores the significance of automation and the use of machine-readable formats for authorization and ConMon artifacts. The new guidance will create a system for automating security assessments and reviews, as well as expand on the initiative to obtain FedRAMP security artifacts solely through automated, machine-readable processes. The General Services Administration (GSA) also plans to update ConMon processes within 180 days and exclusively accepting machine-readable artifacts within 18 months.
Automation and Continuous Monitoring (ConMon) stand at the forefront of FedRAMP modernization as the memo underscores the significance of automation and the use of machine-readable formats for authorization and ConMon artifacts. The new guidance will create a system for automating security assessments and reviews, as well as expand on the initiative to obtain FedRAMP security artifacts solely through automated, machine-readable processes. The General Services Administration (GSA) also plans to update ConMon processes within 180 days and exclusively accepting machine-readable artifacts within 18 months. 