The 2025 Global Cyber Innovation Forum served as a premier gathering where cybersecurity’s most pressing challenges meet collaborative solutions.
Hosted by Forgepoint Capital, Snowflake, Forescout, Google Cloud and Carahsoft at the Embassy of Canada in Washington, D.C., the Forum brought together a curated audience of influential cyber leaders from across the globe, including industry executives, Government officials, policy leaders, venture capitalists and thought leaders from academia and the non-profit sector.
This annual event provided a platform for critical discussions on emerging threats, technological innovation and strategic partnerships essential for securing our digital infrastructure. Five key themes stood out throughout the sessions:
- National Security Threats with Supply Chain Vulnerabilities
- The Rise and Race to AI Dominance
- The Edge of Quantum Transformation
- Typhoon of Attacks on Critical Infrastructure
- Streamlining Cybersecurity Compliance
National Security Threats with Supply Chain Vulnerabilities

The digital supply chain, specifically software and applications civilians use, have increasingly become a source of critical national security vulnerabilities. Government officials and industry leaders warn that software and digital platforms sourced from foreign adversaries have reshaped the threat landscape by implanting foreign influence in the U.S. technology ecosystem.
Technology serves as a funding mechanism for adversaries and comes with a hidden price of mass data collection, making it easier for threat actors to access sensitive information and transform traditional cyberattacks. The lack of transparency in certain nation-states raises concerns on regulatory consequences, potentially giving adversaries a strategic edge in information warfare and creating a blind spot in the global tech supply chain.
U.S. leaders emphasize the necessity for regulated technology supply chains and accelerated Federal certifications, specifically FedRAMP, to ensure innovation does not come at the cost of national security.

Rise and Race to AI Dominance
With the rise of artificial intelligence (AI), data has become the modern form of power. Foreign adversaries are striving to build or gain access to data pipelines to fuel their AI models, bypassing privacy in a way that allows them to train AI models much faster than has been possible in America. The U.S. must counter this by accelerating our own AI model training and innovation, while safeguarding privacy and data integrity.
Government and industry experts state that AI is being underutilized across U.S. operations. The current administration has streamlined AI usage through Executive Order 14179: Removing Barriers to American Leadership in Artificial Intelligence and Executive Order 14277: Advancing Artificial Intelligence Education for American Youth. Additionally, AI should be deployed when combating advanced cyberattacks and automating routine cybersecurity efforts such as threat detection, incident response and vulnerability identification.
The Edge of Quantum Transformation
Emerging technologies such as quantum computing are rapidly approaching mainstream adoption. The massive amount of encrypted data currently stored in secret could be vulnerable to decryption within the next 5 to 10 years. This hovering threat has made the development and deployment of post-quantum cryptography a top priority for the U.S. Government. The race to post-quantum cryptography and quantum computers has not just been an urgency for the U.S. and its allies, but also for adversarial nation-states.

Typhoon of Attacks on Critical Infrastructure
Advanced persistent threat (APT) groups such as Salt Typhoon, Volt Typhoon and Flax Typhoon have already infiltrated critical infrastructure systems, often using “living off the land” techniques. These public and well documented attacks are considered digital terrorism, disrupting U.S. critical infrastructure operations and stealing intellectual property.
In response, the U.S. Government is prioritizing cyber hygiene, secure-by-design and the development of an integrated and robust defense system. Agencies, technology providers and critical infrastructure operators are heavily encouraged to collaborate through information sharing, adoption of emerging technologies and routine threat assessments. The severity of these cyberattacks have increased substantially, highlighting the urgency for a more proactive and coordinated national response from the U.S. Government.
Streamlining Cybersecurity Compliance

The current cybersecurity regulatory landscape presents a fragmented maze of overlapping requirements that hinder both innovation and effective security implementation. Government and industry security teams are overwhelmed by conflicting standards across Federal, State and agency-specific frameworks. Organizations must navigate multiple compliance frameworks—FedRAMP, National Institute of Standards and technology (NIST) requirements, Cybersecurity Maturity Model Certification (CMMC) and various state requirements—creating redundant processes that drain resources without enhancing security.
To address this, industry leaders are advocating for regulatory harmonization initiatives. Federal agencies are working to align various compliance frameworks while updating modernization strategies to build interoperability. By aligning around core standards like NIST 800-53 and implementing automated compliance tools, agencies can reduce complexity while maintaining robust cybersecurity postures. Forum participants agreed: harmonized regulations are essential to enabling secure innovation without compromising oversight.
The Global Cyber Innovation Forum demonstrated that securing America’s digital future requires unprecedented coordination between Government agencies, private industry and international allies. As adversaries continue exploit emerging technologies, the U.S. must respond with unified strategies that streamline regulations, accelerate innovation and sustain global cyber leadership. The insights shared offer a critical roadmap for defending against tomorrow’s threats in a rapidly evolving digital landscape.
Visit Carahsoft’s Resource Hub to dive deeper into the key takeaways, expert perspectives and resources from the 2025 Global Cyber Innovation Forum.



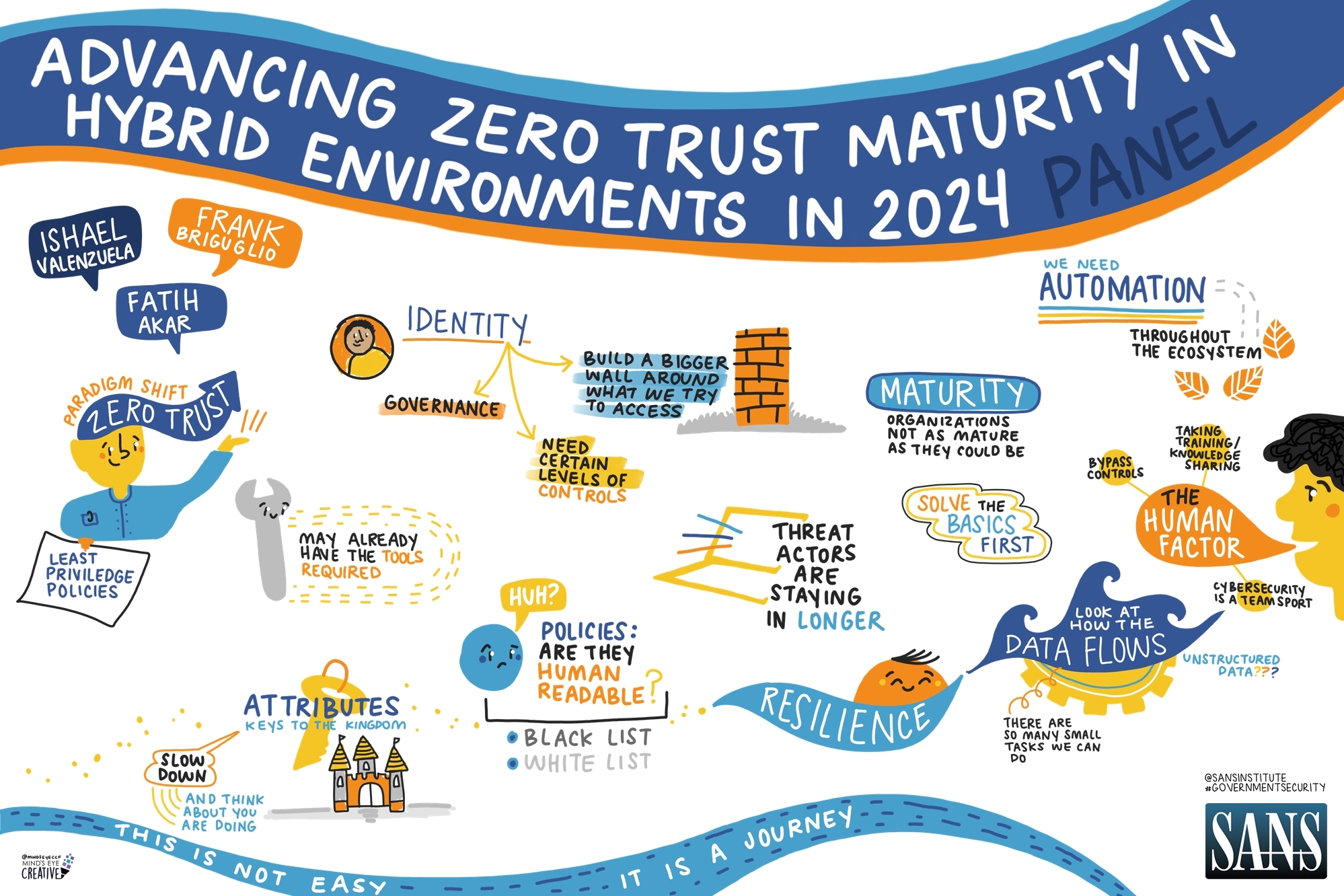
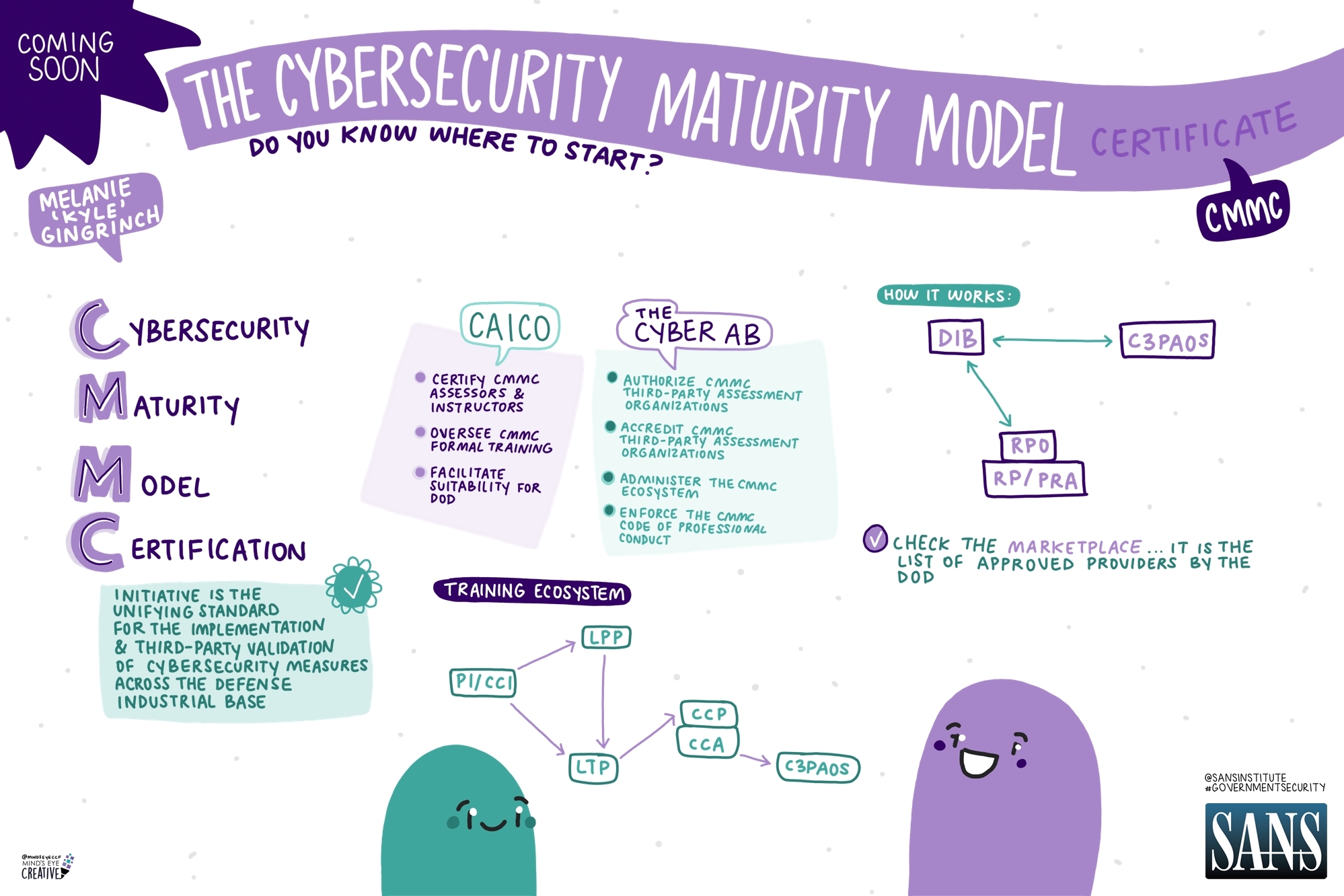
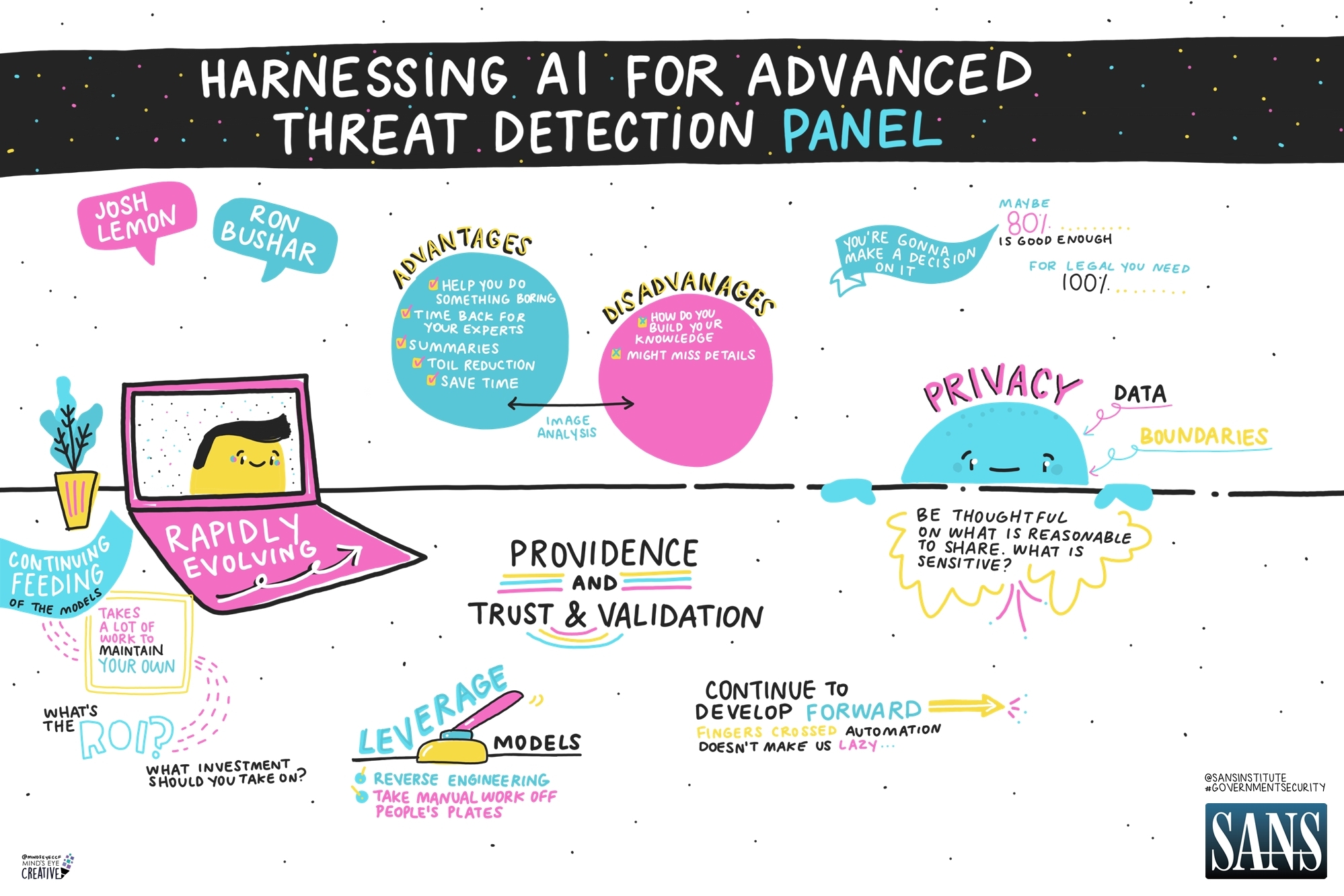

 With ransomware supply chain attacks, bad actors will attack the network of a small supplier and require a ransom from both the organization and the larger beneficiaries up the chain. Ransomware attacks have had a 105% increase, while the average cost of remediating such an attack has more than doubled.
With ransomware supply chain attacks, bad actors will attack the network of a small supplier and require a ransom from both the organization and the larger beneficiaries up the chain. Ransomware attacks have had a 105% increase, while the average cost of remediating such an attack has more than doubled. In version 2.0, a few other significant changes have been made. For example, level one will require an annual self-assessment and affirmation by company leadership. Level two will be split into two groups. In the first group, self-assessment is allowed, and an annual company affirmation will also be required. In the second group, third party assessment will be necessary and will apply to contractors that handle critical national security information. Due to limitations of the third party assessment ecosystem, the DoD has prioritized this second group handling critical national security information for independent assessment. Level three is still under development, but will be based on the NIST 800-172 guidelines. These guidelines are to protect Controlled Unclassified Information (CUI), and outline security enhancements above and beyond the guidelines of NIST 800-171.
In version 2.0, a few other significant changes have been made. For example, level one will require an annual self-assessment and affirmation by company leadership. Level two will be split into two groups. In the first group, self-assessment is allowed, and an annual company affirmation will also be required. In the second group, third party assessment will be necessary and will apply to contractors that handle critical national security information. Due to limitations of the third party assessment ecosystem, the DoD has prioritized this second group handling critical national security information for independent assessment. Level three is still under development, but will be based on the NIST 800-172 guidelines. These guidelines are to protect Controlled Unclassified Information (CUI), and outline security enhancements above and beyond the guidelines of NIST 800-171. If they aren’t, then we might not actually want to completely deny access. Today’s workforce is highly mobile, and we must take that into account while building applications. If we limit access so tightly that nobody can use it or they need a very specific environment to use it, then our users will find different solutions.
If they aren’t, then we might not actually want to completely deny access. Today’s workforce is highly mobile, and we must take that into account while building applications. If we limit access so tightly that nobody can use it or they need a very specific environment to use it, then our users will find different solutions. Supporting the Law Enforcement Community During COVID-19 and Beyond
Supporting the Law Enforcement Community During COVID-19 and Beyond