Carahsoft Technology Corporation, a leader in Government IT solutions, partnered with the SANS Institute for the fourth year in a row to host the 2024 Government Security Solutions Forum. The event gathered cybersecurity professionals and Public Sector leaders to address evolving cyber threats facing Government agencies. Experts led discussions on key topics, including Zero Trust implementation, achieving Cybersecurity Maturity Model Certification (CMMC) compliance and harnessing artificial intelligence (AI). This blog highlights key takeaways from three of the six sessions surrounding these imperative industry topics, providing actionable insights to strengthen cybersecurity defenses in today’s digital landscape. During the event a visual artist Ashton Rodenhiser summarized the sessions which are featured in this blog.
Zero Trust Implementation
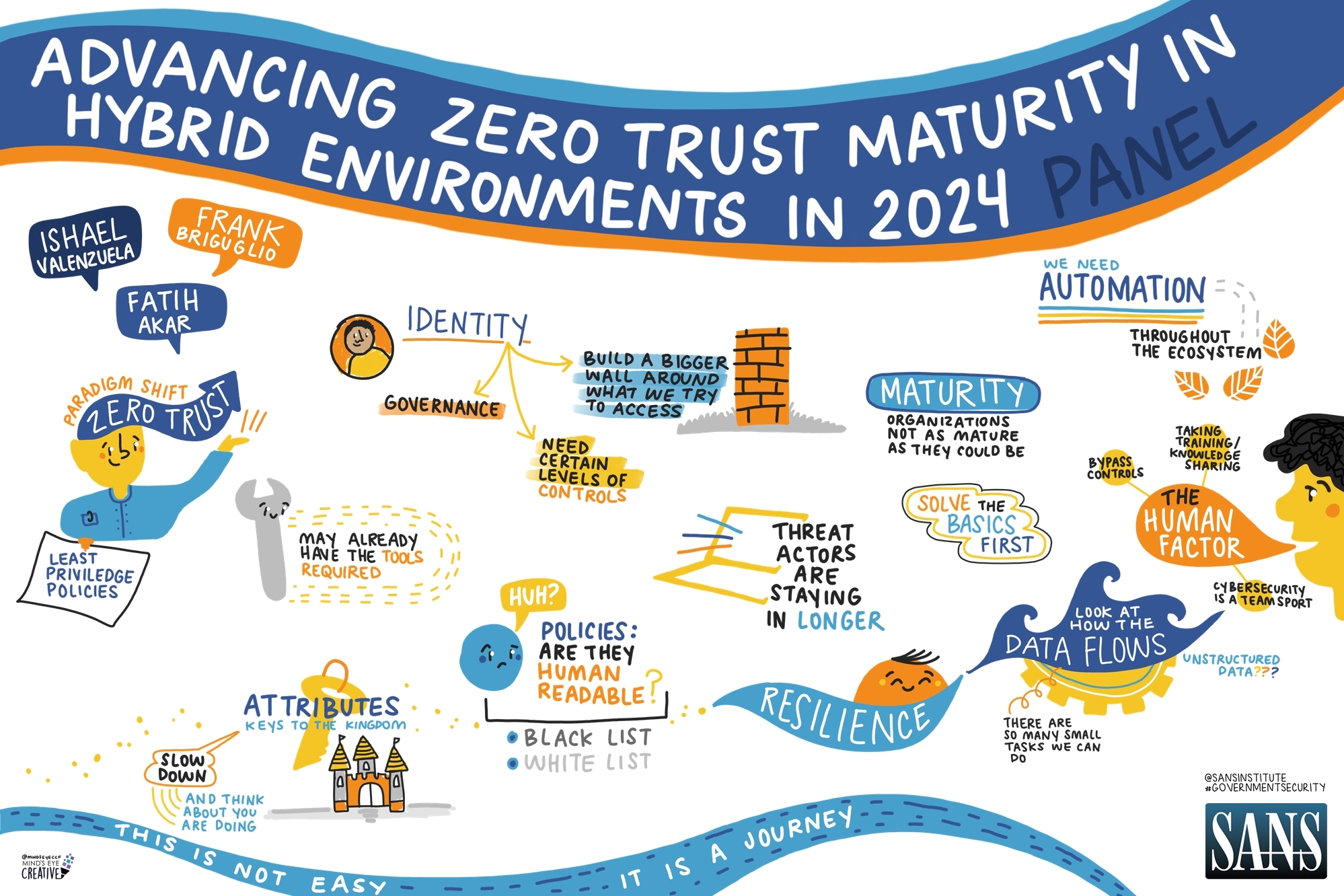
During the session “Zero Trust Implementation Strategies,” experts explored the growing challenges security professionals face with emerging technologies and provided key insights into building a robust Zero Trust framework.
As new technologies rapidly emerge, security professionals face increasing challenges in keeping pace, especially with the integration of on-prem environments and the cloud. A key principle of Zero Trust is the enforcement of least privilege policies, which requires a shift in how identity management is applied. This begins with strong governance to ensure the accuracy and reliability of policies and attributes.
Building a comprehensive security framework also involves implementing contextual authorization through micro-segmentation, considering factors like device, location and time to create a robust protective barrier. Furthermore, integrating identity management with Endpoint Detection and Response (EDR) tools is becoming increasingly important for tracking authorized processes and addressing the extended presence of threat actors who exploit admin identities to execute malware.
One of the biggest challenges in managing security policies is their complexity. Many security policies lack human readability due to their intricate structure, making automation essential for managing actions and enforcing compliance. The National Security Administration’s (NSA) recent Zero Trust guide emphasizes automation as a key pillar, highlighting its importance in responding to data flow deviations and maintaining security.
Despite the advanced systems in place, human error continues to be a major vulnerability. Employees can unknowingly compromise security through phishing attacks or by interacting with malicious links. To mitigate this, organizations must prioritize improving employee awareness and addressing the human factor as a critical component of cybersecurity.
Explore how Carahsoft’s Zero Trust portfolio can help Government implement a comprehensive Zero Trust strategy, strengthening organization’s security and protecting critical assets.
Achieving CMMC Compliance
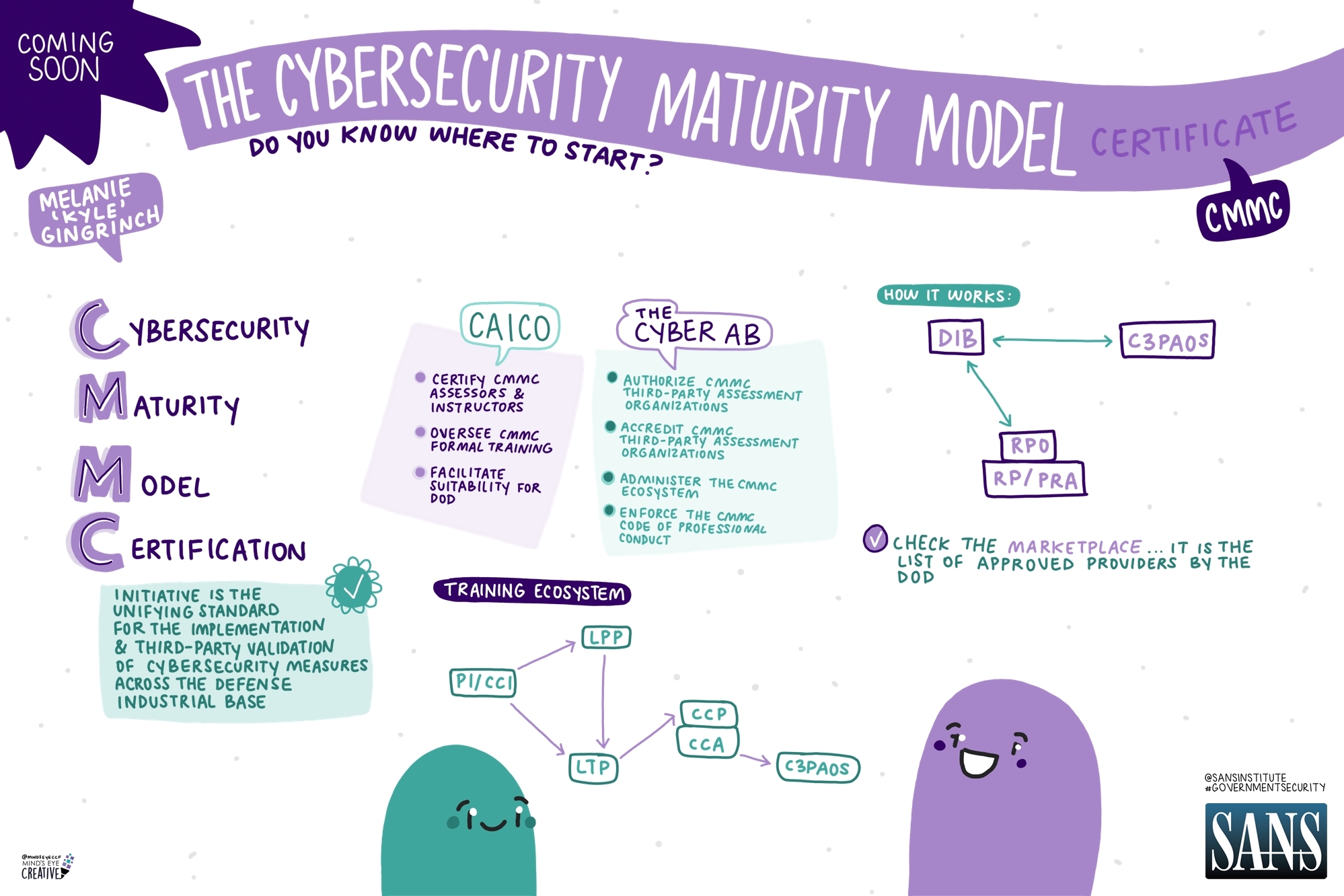
The session “Navigating Supply Chain Security and CMMC Compliance” provided valuable insights into the upcoming implementation of the CMMC framework and its implications for Defense Industrial Base (DIB) organizations. This certification will ensure that DIB organizations meet stringent cybersecurity standards through third-party assessments and will soon be mandatory for both prime contractors and subcontractors working with the Department of Defense (DoD).
CMMC consists of multiple certification levels, with Level 1 covering basic practices for Federal Contract Information (FCI) and Level 2 addressing 110 practices based on NIST 800-171, extending to around 320 actions. To prepare, organizations should work with Registered Practitioner Organizations (RPOs) to assess their readiness. These RPOs employ Certified CMMC Professionals (CCPs) and Certified CMMC Assessors (CCAs), who are trained and certified by the Cybersecurity Assessor and Instructor Certification Organization (CAICO), a subsidiary of Cyber AB, which oversees the curriculum and training programs.
After preparation, organizations will undergo an official assessment by a CMMC Third-Party Assessment Organization (C3PAO), which hires CCPs and CCAs to evaluate the cybersecurity measures in place. As the CMMC rule takes effect, organizations must ensure they work with certified professionals listed on the Cyber AB marketplace, as uncertified entities will not be recognized by the DoD.
Given the complexity of CMMC and the fact that preparation for certification can take at least six months, organizations are encouraged to start early to meet the new requirements.
Carahsoft is proud to be part of the CMMC ecosystem, with around 800 employees focused on cybersecurity and partnerships with over 150 vendors. By closely tracking policies and industry trends, Carahsoft aligns customer needs with relevant technologies, promoting “better together” integrations to maximize the value of existing investments. Carahsoft works with vendors that address every CMMC maturity level and capability domain, guiding customers through the complex decision-making process to ensure that they select the most suitable technologies to fill security gaps effectively and efficiently. Explore Carahsoft’s CMMC portfolio.
Harnessing AI
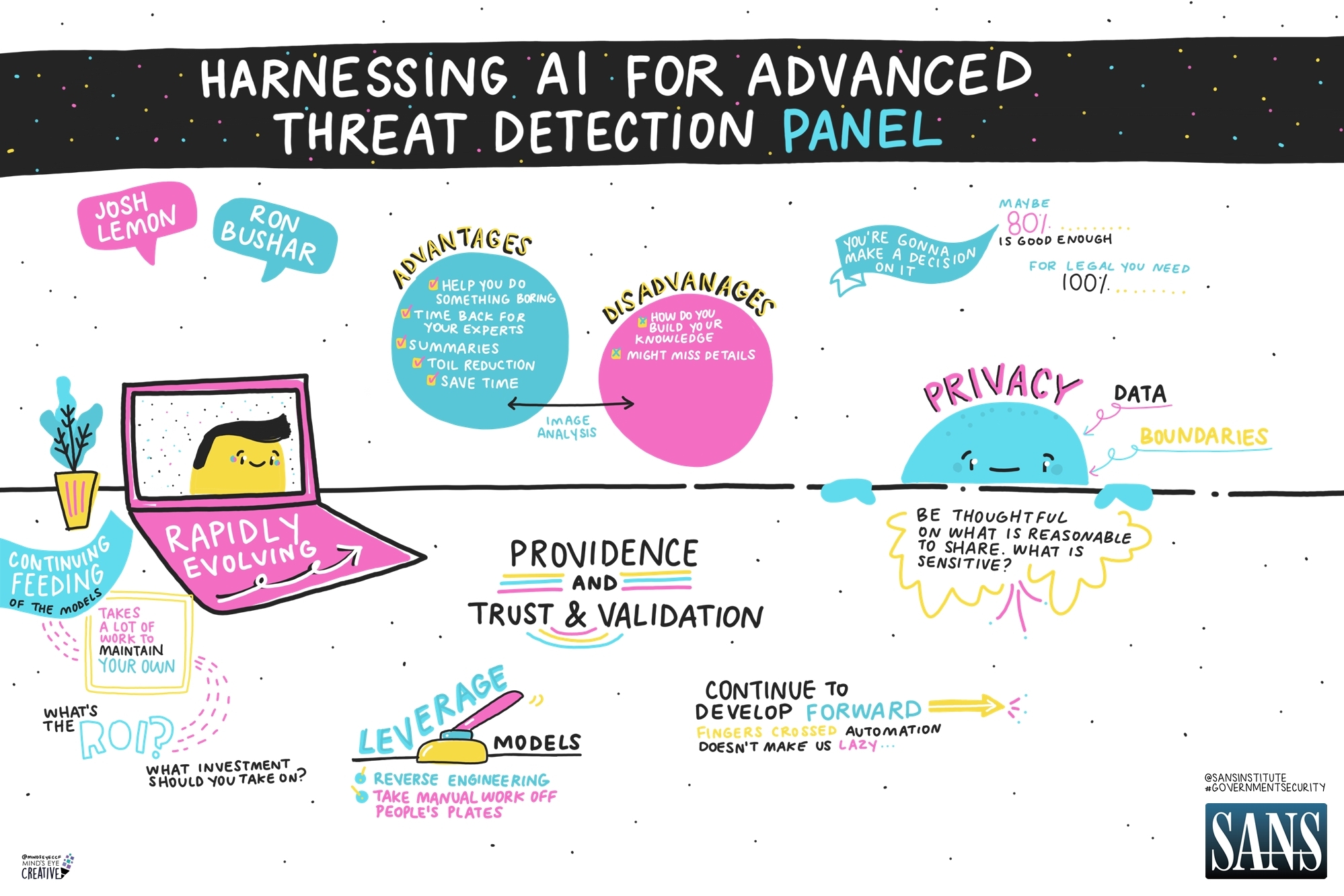
Amid the complexities of cybersecurity, effective threat detection and response are increasingly reliant on advanced technologies like AI. The session “Harnessing AI for Advanced Threat Detection” explored the benefits and risks of integrating AI into security operations, highlighting key strategies for balancing automation with rigorous security practices.
“Advanced threat detection” spans various aspects of security operations, including the development and collection of threat intelligence. AI offers significant benefits in early threat detection, helping organizations quickly identify and respond to malicious activity. However, its use must be approached cautiously across the entire security chain.
With the rise of generative AI, industries are applying AI to automate time-consuming tasks. A key benefit is AI’s ability to condense information quickly. Tasks like threat searching or intelligence analysis, which once took hours, can now be completed in minutes, freeing experts to focus on higher-level tasks. This “toil reduction” is vital, as AI automates routine work and creates immediate efficiencies with minimal effort.
While AI brings advantages, there are inherent risks in implementing AI models and infrastructure. It is crucial to approach AI from two perspectives: using it to enhance security while ensuring the security of AI itself.
Organizations must also consider how they can trust AI-generated information. Trust and validation are essential. Provenance—knowing the source of data and models—is key to building confidence. While AI can handle most of the work, experienced engineers and analysts are still needed to verify and analyze the results so security teams can focus on more complex matters.
The siloed nature of work within security operations may limit intelligence sharing. Maintaining control of input data is critical, especially with public models hosted by technology vendors. If training data enters public models, organizations may compromise sensitive information. In regulated environments, private models offer safer options, allowing companies train AI while retaining control.
When integrating AI into security operations, organizations should build trust by validating each use case, allowing AI to be operationalized while ensuring accuracy. Experimentation is key to identifying where AI can provide a return on investment. However, implementing AI requires careful consideration of security models, AI safety and governance, particularly as organizations scale AI into operations.
Unlock the potential of AI to drive innovation and efficiency in Government organizations with Carahsoft’s AI and machine learning portfolio.
Frank Briguglio, Federal CTO at SailPoint, and Fatih Akar, Security Product Manager at VMRay, led the discussion on Zero Trust. Melanie ‘Kyle’ Gingrich, Interim Executive Director at The Cyber AB, provided guidance on navigating CMMC compliance. Josh Lemon, Director of Managed Detection and Response at Uptycs, and Ron Bushar, Managing Director of Mandiant Solutions at Google Public Sector, explored the role of AI in advanced threat detection.
Explore more insightful sessions on how Public Sector cybersecurity teams are strengthening their security posture by watching the SANS 2024 Government Security Forum in partnership with Carahsoft.



 With ransomware supply chain attacks, bad actors will attack the network of a small supplier and require a ransom from both the organization and the larger beneficiaries up the chain. Ransomware attacks have had a 105% increase, while the average cost of remediating such an attack has more than doubled.
With ransomware supply chain attacks, bad actors will attack the network of a small supplier and require a ransom from both the organization and the larger beneficiaries up the chain. Ransomware attacks have had a 105% increase, while the average cost of remediating such an attack has more than doubled. Supply Chain Attack Scenarios
Supply Chain Attack Scenarios On the hardware side, there are two contracts. One is the Army desktop and mobile computing contract and the other is ITES-3H, which is the Army Information Technology Enterprise Solutions-3 Hardware contract. From the services side, there is ITES-3S, Army Information Technology Enterprise Solutions-3 Services. For software, it is ITES-SW, Army Information Technology Enterprise Solutions – Software.
On the hardware side, there are two contracts. One is the Army desktop and mobile computing contract and the other is ITES-3H, which is the Army Information Technology Enterprise Solutions-3 Hardware contract. From the services side, there is ITES-3S, Army Information Technology Enterprise Solutions-3 Services. For software, it is ITES-SW, Army Information Technology Enterprise Solutions – Software.