As the end of the SLG and EDU fiscal year approaches, State and Local Governments and education institutions are ramping up purchasing to ensure every allocated budget dollar is spent and their organization is prepared for further IT advancements in the coming year. Leveraging the right contract vehicles can streamline procurement processes, ensuring timely and efficient acquisition of necessary technologies and services. These contracts can also provide technology vendors and resellers unique opportunities to expand their Public Sector businesses.
Below, we explore the top contract vehicles that State and Local Governments (SLG) and education institutions (EDU) are using as they close out their fiscal year with their preferred reseller partner this month.
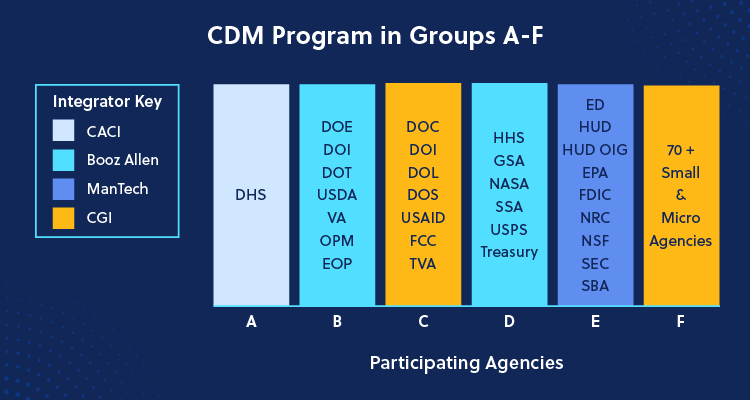
1. NASPO ValuePoint
NASPO ValuePoint is the cooperative purchasing arm of the National Association for State Procurement Officials, designed to provide access to the best possible IT solutions. It is considered to be the nation’s most significant public contracting cooperative. The contract offers a wide variety of cloud solutions, including IaaS, PaaS and SaaS.
Carahsoft’s Contract: NASPO ValuePoint contract #AR2472 includes thousands of technology vendors.
Who Can Use It: State and Local Governments, municipalities and public education entities (K-12 and Higher-Education).
2. GSA Cooperative Purchasing Program
The General Services Administration (GSA) Cooperative Purchasing Program grants State and Local Government entities access to Federal GSA Schedule contracts for IT solutions and professional services. The GSA Cooperative Purchasing Program provides a streamlined procurement process for State and Local Governments to purchase IT solutions, often with pre-negotiated and cost-effective pricing structures.
Carahsoft’s Contract: GSA Schedule #47QSWA18D008F, aggregates solutions from many technology vendors.
Who Can Use It: State and Local Governments.
3. Texas Department of Information Resources (TX DIR)

The Texas Department of Information Resources (TX DIR) has established a Cooperative Contracts Purchasing Program which offers a wide range of product offerings, services and technology solutions to Public Sector customers in Texas and nationwide. The DIR contracts streamline the procurement process by handling all of the preliminary work upfront, making it easier for eligible entities to acquire a wide range of hardware, software, cloud solutions and professional IT services. Public organizations outside of Texas are also eligible to purchase through DIR contracts.
Carahsoft Contract: Carahsoft holds seven TX DIR contracts, offering a wide variety of products and services from hundreds of technology vendors.
Who Can Use It: State and Local Governments, public education and other public entities nationwide.
4. California Software Licensing Program (CA SLP)
The California Software Licensing Program (CA SLP), established in 1994 and administered by the Department of General Services’ Procurement Division provides State and Local Government entities within the state of California with access to discounted software licensing agreements. This vendor held contract expedites and simplifies the procurement process while supporting State Government modernization goals with a host of technology solutions.
Carahsoft Contract: Carahsoft acts as a reseller on 19 CA SLP contracts, offering solutions ranging from data management to cybersecurity and more.
Who Can Use It: State and Local Government agencies in California.
5. E&I Cooperative Services
E&I Cooperative Services is the largest and most experienced member-owned, non-profit purchasing cooperative focused on education. E&I provides education institutions with access to IT products and services, including learning management systems, classroom technologies and administrative software tailored to their unique needs.
Carahsoft Contract: E&I Cooperative Services contract #EI00063-2021MA provides E&I members with cloud and managed service solutions and related IT products and services.
Who Can Use It: Educational institutions, including K-12 schools, teaching hospitals, colleges and universities.
6. OMNIA Partners Public Sector
OMNIA Partners is one of the largest Public Sector cooperative purchasing organizations, providing comprehensive access to a wide variety of technology contracts across hardware, software and cloud solutions. The cooperative purchasing program is focused on efficiency, compliance and value, aiming to further streamline the procurement process for the Public Sector entities that leverage this contract.
Carahsoft Contract: Carahsoft’s contracts with OMNIA Partners, #R240303 and #23-6692-01, provide State and Local Governments and education institutions with access to technology from over 150 vendors.
Who Can Use It: State and Local Governments, public education institutions and nonprofits that are approved OMNIA partners.
7. The Quilt
The Quilt is a national coalition of advanced regional networks for research and education, providing members with access to IT services and technologies. The Quilt provides access to technologies that meet the specific needs of educational and research communities, offering high-performance computing, research networking and related IT services to hundreds of universities and thousands of other education institutions.
Carahsoft Contract: MSA – 05012019F offers members with access to networking, cloud infrastructure, data management, cybersecurity, virtualization and enterprise technologies.
Who Can Use It: Higher education institutions, research institutions and related organizations.
By turning to these popular contract vehicles, State and Local Governments and education institutions can easily find and purchase technologies that map to their modernization efforts while ensuring compliance and maximizing investments through their preferred resellers. As the fiscal year draws to a close, these contracts serve as a vital resource for timely and cost-effective procurement, driving end-of-year business to new heights and propelling Public Sector advancements.
For more information on Carahsoft’s offerings under each of these contract vehicles, please reach out to contracts@carahsoft.com.