The Continuous Diagnostics and Mitigation (CDM) Program, established in 2012 by the Cyber Security Infrastructure Security Agency (CISA), provides a dynamic approach to fortifying the cybersecurity of Government networks and systems by improving security posture of participating agencies and mitigating risk to the nation’s cyber and physical infrastructure.
Carahsoft’s long and supportive history of CISA’s CDM program allows Carahsoft to provide cutting edge software to benefit the governments pressing national security requirements. Currently, Carahsoft supports more than 70 vendor partners on the CDM Approved Products List, assisting in completing the submission process and maintaining communication with CISA for APL updates. Our extensive vendor and partner network allows the Government to procure asset and identity management, network security and data protection tools in support of the CDM program.
How the CDM Program Works
The goal of the CDM program is to find and prioritize risks in cybersecurity, increasing visibility into the Federal cybersecurity space and improving the Government’s ability to respond to issues or threats. In the past few years, the CDM program has grown to become a proactive, coordinated and efficient entity. In CISA’s projected budget for 2025, $469.8M will be allotted for the CDM program to strengthen the security posture of Federal Government networks and systems.

CISA has a congressional mandate at the national level to extend cybersecurity and the availability of CDM tools. It also supplies capabilities and knowledge into the framework of State and Local Governments and works to protect the nation’s vital infrastructure. Government agencies have specific funding that they can use—in essence as a grant. Different agencies and governmental entities can apply to get funding from the Department of Homeland Security (DHS) to enable the purchase of CDM technologies. DHS and CISA work with emerging, established and developing cyber technologies to counter threats from a wide variety of adversaries.
The CDM Program APL and Procurement Process
The CDM program offers a set of certified tools and sensors, known as the APL. To begin the process for a solution to be approved for the APL, a vendor must submit information about its capabilities to CISA. For example, where that tool sits in the network and what it is capable of. Tools that are part of the CDM program provide capabilities in the following 4 areas:
- Asset Management
- Identity and Access Management
- Network Security Management
- Data Protection Management
The CDM office at CISA evaluates the offeror’s claims for that solution for acceptability and applicability onto the APL. If it meets the defined cybersecurity criteria, it is then classified into a specific category. Products labeled by CDM listed on the GSA MAS IT schedule through GSA Advantage have already been vetted and approved by CISA, signifying that they meet the technical standards needed for Government procurement. Therefore, agencies do not need to repeat the evaluation process when purchasing through GSA. While CISA manages the CDM program, GSA provides the ease of buying and the ability to expedite awards. CDM products can also be acquired through the NASA SEWP CDM catalog and are added to this contract via customer request.
The CDM program includes cybersecurity tools and sensors reviewed for conformance with Section 508, Federal license users and CDM technical requirements. Each month, the program offers a weeklong submission window for new tools to be submitted for addition to the APL, which allows for unique flexibility for a Government program and strengthens the program over time. Since the acquisition of new and innovative technology can oftentimes lead to longer implementation timelines for the Government, monthly rolling submissions allow for a quicker and more flexible process for agencies obtaining new products. Not only is this a benefit for Government, but for industry, too, as a larger submission window allows technology vendors the opportunity for their products to be added to the APL more frequently.
Cybersecurity threats are ever evolving—and consequently so are the tools and the defensive measures needed to mitigate them. CDM products expire from the APL every 3 years to ensure the products listed continuously comply with modern cybersecurity standards. For more information on the technical evaluation process, please review the APL Product Submission Instructions.
Benefits of Acquiring CDM Tools for End Users
Broad Base of Customers: The CDM program focuses on Federal infrastructure but works with GSA and its broad customer base, including buyers such as the Departments of Agriculture, Transportation, Justice and Education, as well as tribal and territorial Governments, for example.
High Levels of Support: At CISA, the CDM program delivers high levels of support to Federal civilian agencies. It has direct program management resources, funding resources, and outreach resources, among others.
Election Security: Election security is top of mind for 2024. The Help America Vote Act (HAVA) is an organization whose funding focuses on securing elections, ensuring confidence in election results, having robust voting technology and withstanding potential cyber threats. This is a bipartisan issue since all parties agree that user experience and cybersecurity require improvement. The CDM program and its robust suite of tools address these crucial objectives.
Critical Infrastructure: DHS prioritizes protective services to critical infrastructure organizations like power companies, oil refineries and railroads. For example, $130.3M of CISA’s FY25 budget will ensure emergency communication interoperability and assistance.
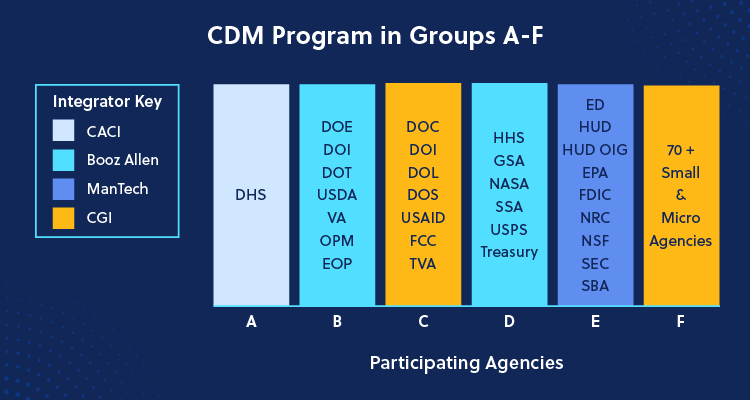
Integrators for the CDM Program
Integrators are an integral part of the CDM Program, providing cybersecurity expertise, consulting, technology, tools, solutions and services to participating Government agencies. These organizations work directly with the agencies to strengthen IT security posture, zero trust maturity and other mission critical cybersecurity needs. The following integrators are currently the contract holders for agencies participating in the CDM Program in groups A-F, which are categorized by the task orders each agency holds.
To learn more about defending Federal networks and systems with the CDM Program, the partners we support on the CDM APL and how you can sell your products under CDM, visit our CDM Program Overview and contact us today.

 GSA is currently engaged in an activity called MAS Consolidation, enabling a new single solicitation process that streamlines terms and conditions across multiple schedule programs. This new process is GSA’s effort to make it easier for both industry and government to contract by having a single, consolidated set of terms. Previously, there were separate schedules for different commodity types, i.e. furniture, office supplies, or software. Consolidation of the varied schedules will enable customers to find total solutions under one contract vehicle while ensuring that necessary terms and conditions are met.
GSA is currently engaged in an activity called MAS Consolidation, enabling a new single solicitation process that streamlines terms and conditions across multiple schedule programs. This new process is GSA’s effort to make it easier for both industry and government to contract by having a single, consolidated set of terms. Previously, there were separate schedules for different commodity types, i.e. furniture, office supplies, or software. Consolidation of the varied schedules will enable customers to find total solutions under one contract vehicle while ensuring that necessary terms and conditions are met.