FormAssembly’s data collection platform lets you gather data, build workflows, and improve efficiency with a no-code, form-based solution that can be up and running in minutes. With FormAssembly, users have a powerful, easy-to-use solution for collecting, managing, and leveraging data.
FedRAMP-Ready Form Building and Data Collection
FormAssembly is an enterprise data collection platform that enables government agencies to securely collect data, automate workflows, and improve efficiency. Our no-code form builder and Salesforce-connected web forms can be up and running in minutes, so you can collect data with ease and securely store information in a central location. Our Government plan is FedRAMP-Ready and offers PCI DSS Level 1 certification, compliance with data privacy laws (GDPR, CCPA, etc.), and advanced data oversight tools in our Sensitive Data Management feature.

FormAssembly’s data collection platform lets you gather data, build workflows, and improve efficiency with a no-code, form-based solution that can be up and running in minutes. With FormAssembly, users have a powerful, easy-to-use solution for collecting, managing, and leveraging data.
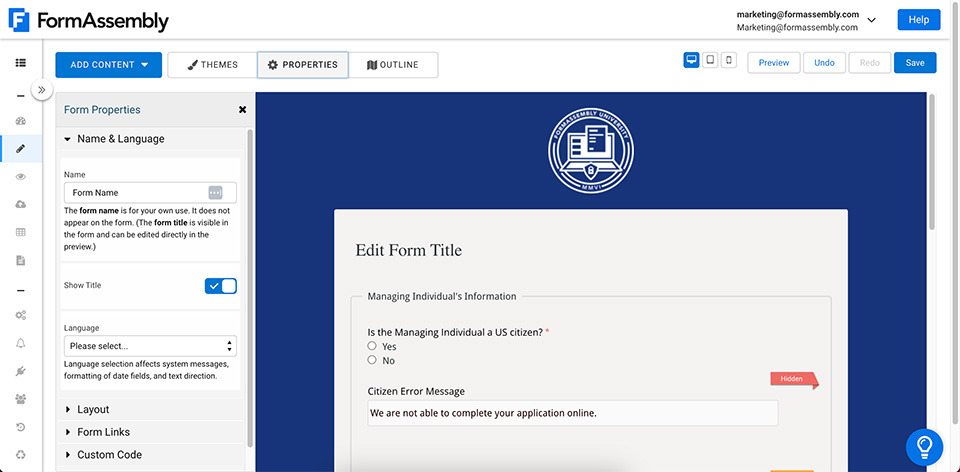
Build Forms Fast with No-Code Tools
The no-code form builder allows you to quickly build and launch secure web forms that integrate directly with Salesforce and other business-critical tools. Simply drag and drop form fields, add validation rules and sensitive data features, connect to business-essential tools, and more — all without adding a line of code. You’ll be able to reduce manual work, eliminate data silos, and address security concerns common with paper forms and spreadsheet processes.

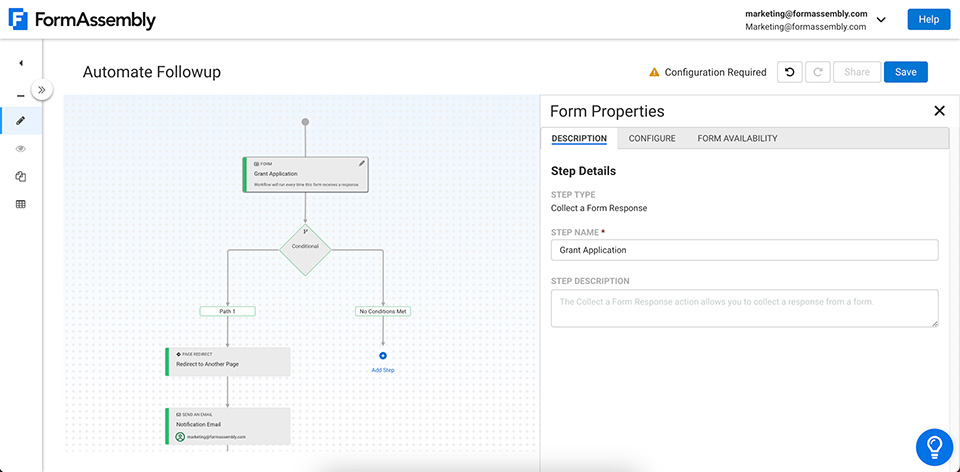
Automate Data Processing
Use FormAssembly Workflow, the no-code visual process builder, to effortlessly build and automate complex processes involving multiple forms, respondents, email notifications, and more. Workflow enables form-to-form prefilling, branching pathways with multiple conditions, assigning form responses and tasks, and custom data purge settings. You can easily add multiple integrations to a workflow and send various data types, including response PDFs and e-signatures, directly into Salesforce. You'll be able to collaborate effectively across teams, make decisions faster, and keep data collection processes running smoothly.

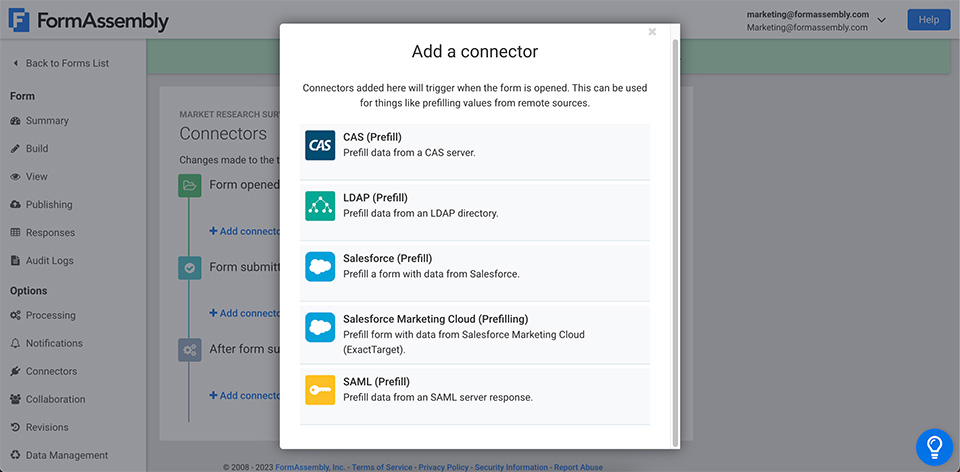
Prefill Forms with Salesforce Data
The Salesforce Prefill Connector allows you to pull data directly from Salesforce into your forms in a variety of text fields, such as dynamic picklists. Respondents won’t have to enter their information multiple times and can update any outdated information in real-time, all of which gets synced back to the Salesforce records. You’ll get access to the most up-to-date information and gain more insight into your data.

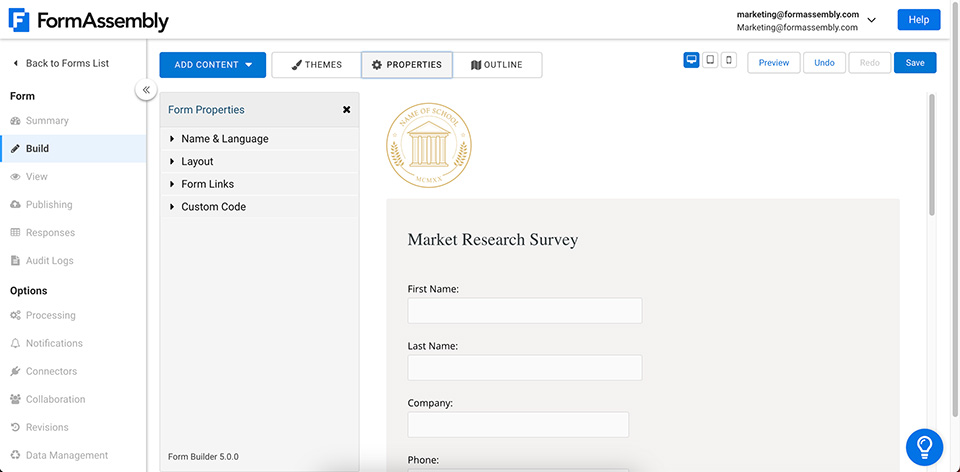
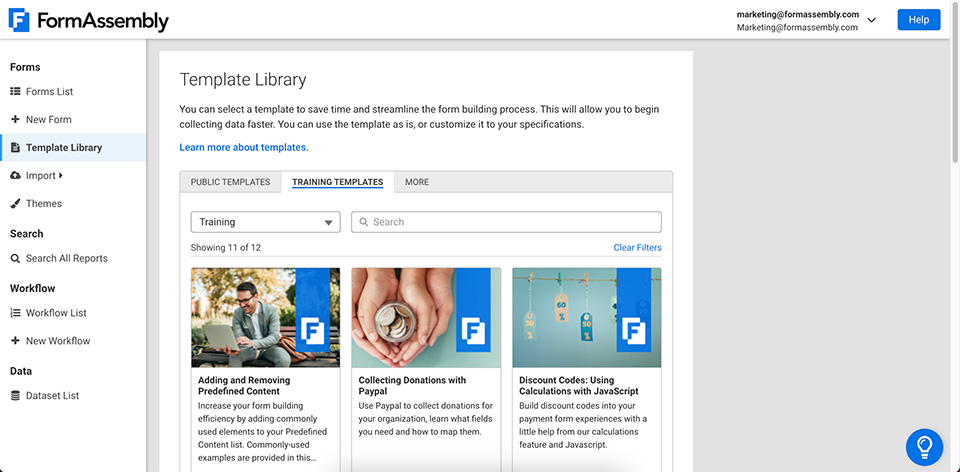
Access Fully-Built Form Templates
The Template Library gives you access to dozens of pre-built forms ready to customize and launch in minutes to expedite your data collection processes. You can choose from templates based on a specific category or add your own custom form for easy access by collaborators.

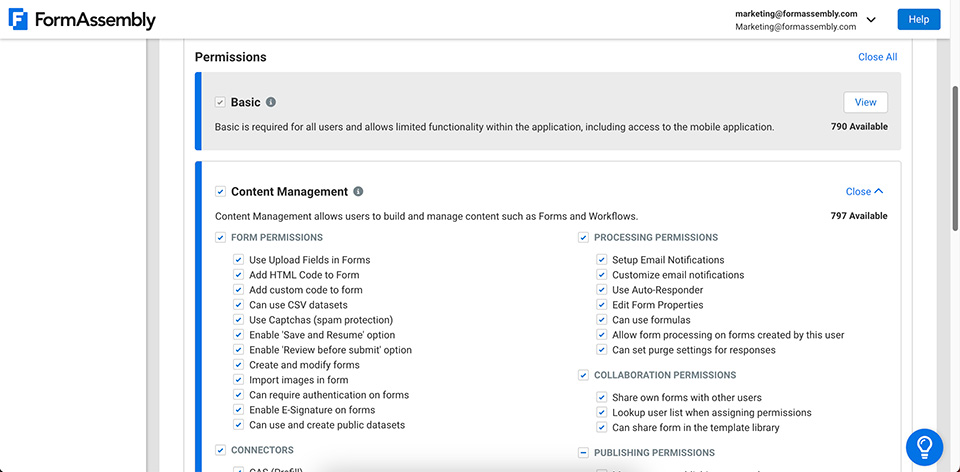
Manage User Access and Permissions
FormAssembly offers four different Permission Packages that administrators can assign as needed based on the tasks and responsibilities of an individual user. Admins will have access to a list of permission sets for each user, providing greater control over who can build and manage forms and workflows, oversee and export form responses, or have full access to the admin dashboard. You’ll be able to maintain better governance over data and minimize the risk of unauthorized data access by users.