The past two years have seen relentless cyberattacks employed by hostile nations to disrupt American security, public health and the economy. The current U.S. administration has announced its emphasis on fighting ransomware particularly within these critical infrastructures. New regulations are underway for 4 of the 16 sectors including healthcare and water, which is a part of the utilities sector.[1] In anticipation of the coming changes, here is a look into the current state of ransomware in healthcare and utilities, both of which have experienced some of the worst cyberattacks in recent years. By understanding the challenges in these fields, IT administrators can work to evaluate their individual organizational cybersecurity status and start to resolve issues before the enforcement of the new regulations begin.
USE CASE: HEALTHCARE
Unlike ransomware attacks on other sectors, cyberattacks within healthcare are threat-to-life crimes instead of economic crimes because they impede hospital operations and critical patient care. Ransomware attacks by foreign cybercriminals on hospitals are analogous to military strikes against healthcare facilities, which violate international warfare laws. Because of this, it is not only an IT system concern but a healthcare-wide risk that must be addressed with grave importance.
Recent Attacks
In 2020, Universal Health Services network was hacked by the Ryuk variant of ransomware resulting in all its IT systems shutting down and operations stopping at 250 hospitals. According to a Department of Health and Human Services (HHS) report, the incident ultimately cost $67 million in lost revenue and recovery although $26 million was covered by cyber insurance.[2]
The devastating ransomware attack against Scripps Health in May 2021 cost the company $112.7 million with over a month of cleanup and extensive revenue loss. [2] In light of this rise in attacks, the Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA) and HHS all issued admonitions that hospitals and health systems be on alert and strengthen their ransomware protection and emergency plans.[3]
Impact
On average, the HHS reported that each healthcare cyberattack cost $10.10 million including the ransom, business loss and remediation costs, ranking it as the most expensive sector for cyberattacks across all industries.[4] This is 41.6% higher than in 2020.[2] Often, criminals target the healthcare sector because of the quantity and sensitivity of data available. Hospitals are also particularly susceptible due to the complexity of the IT infrastructure, 24/7 operations and the strong repercussions to the reputation of the organization, making them more likely to pay the ransom if an attack happens. Many healthcare organizations also employ a lot of legacy equipment and software as well as perform extensive amounts of file-sharing with many vulnerable endpoints. These areas are a security concern but some of these older systems are also imperative for regular operations and certain medical software to run.[4]
In addition to the immediate disturbance of operations, all of these hacks expose millions of patient records. For the general population, these healthcare breaches have tripled in their impact between 2018 and 2021, with 14 million people affected to now over 45 million. According to the HHS, healthcare institutions faced 373 ransomware attacks from January to July 2022.[2] Cyber disruptions’ impact through delayed care in areas with poorer healthcare is magnified even more. Northwell Health’s Senior Vice President and Chief Quality Officer Mark Jarrett says: “Clinicians in general tend to think of this as an information technology issue, and it really isn’t. It’s a patient safety issue.”[5]
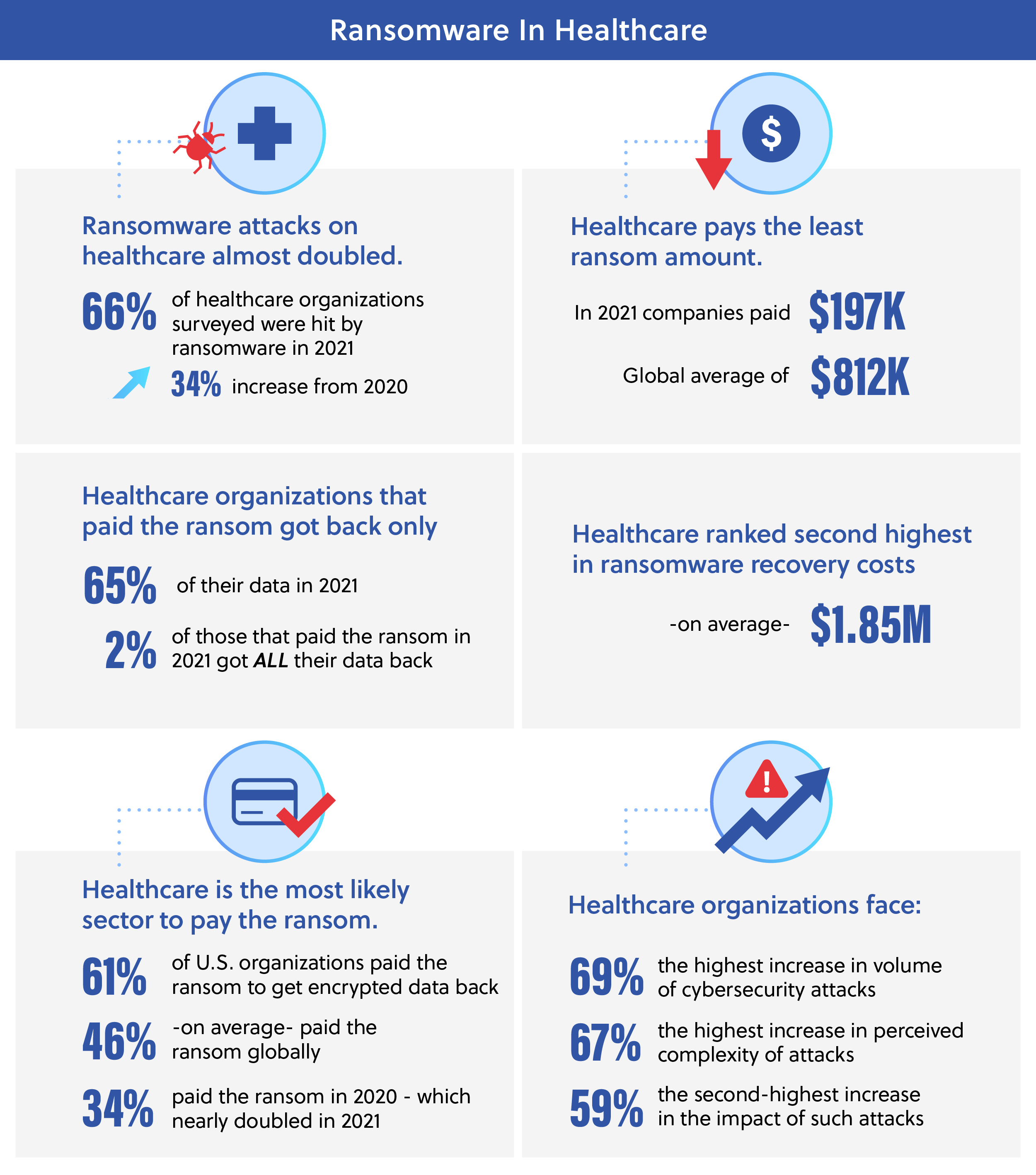
Post-Attack Measures
Because of the unfortunate success of ransomware within healthcare, many institutions are seeking cyber insurance to offset the cost. The high number of incidents, however, has made it more difficult to obtain coverage until substantial cyber security defenses are in place.[6] While 79% of healthcare organizations possess cyber insurance, nearly all of them have had to improve their cybersecurity strategies to maintain coverage including incorporating new technologies, more employee training and other system process changes.[6]
The Censinet and the Ponemon Institute report, “The Impact of Ransomware on Healthcare During COVID-19 and Beyond,” noted that most healthcare institutions budget 3-4% of IT spending towards cybersecurity while financial firms spend an average of 6-14% to combat cybercrimes.[7] When healthcare systems invest in more cyber defenses, the overall impact of ransomware is dramatically lessened. For institutions with fully deployed cyber security measures, an IMB Security’s annual breach report discovered a 65.2% reduction in average breach cost and 74-day shorter detection and containment cycle versus companies without. This decreased the cost from $6.20 million to $3.15 million for those with security and a breach lifecycle of 323 days down to 249.[2] These results speak to the importance of implementing comprehensive cybersecurity protection and remediation tools in the healthcare sector.
USE CASE: UTILITIES
Similar to healthcare, ransomware attacks to the utilities sector are not just costly and inconvenient, they also impede critical infrastructure and have a wide impact radius to public health, safety and the companies’ bottom line. Utilities also underscore every aspect of daily life through electricity, oil, water and natural gas.
Recent Attacks
In May 2021, the Colonial Pipeline attack brought ransomware in utilities to the forefront of the public eye. The incident affected 45% of the fuel supply used on the U.S. East Coast, which generated a steep price increase and public panic.[8] Within two hours of access, the cyber criminals immobilized 100GB of critical data. As a result, the 5,500-mile pipeline system was closed for six days until the company paid $4.4 million in cryptocurrency as ransom. Reuters lists this cyber event as the most disruptive ransomware attack on record.[9]
Following the Colonial Pipeline hack, Congress issued a strong cybersecurity measure requiring critical infrastructure organizations to report an attack in three days and any payment of the ransom within one day. The goal is to increase information sharing and better equip the government to assist in these situations.[10]
Another large cyberattack in 2021 occurred in Florida when cybercriminals infiltrated the water treatment facility’s network through dormant software and spiked the sodium hydroxide level to 100 times its usual amount. Although the attack was detected and neutralized, the event unveiled a huge vulnerability in U.S. water systems due to minimal IT budgets, staffing shortages causing maintenance delays, outdated cybersecurity systems and other factors, making it easier for cybercriminals to breach the system unnoticed. Shortly after the news of the Florida water hack, three additional water treatment plant attacks across the country that had not been reported came to the surface.[11] Research indicates that this situation represents a consistent trend. Although large attacks on well-known businesses are often featured more in the news, small businesses experience more ransomware attacks but they commonly go unreported.[12] The limited resources available often make smaller local government and enterprises a preferred target for ransomware because it is more difficult for them to recover from an attack, thus making them more likely to pay the ransom quickly.[13]
Impact
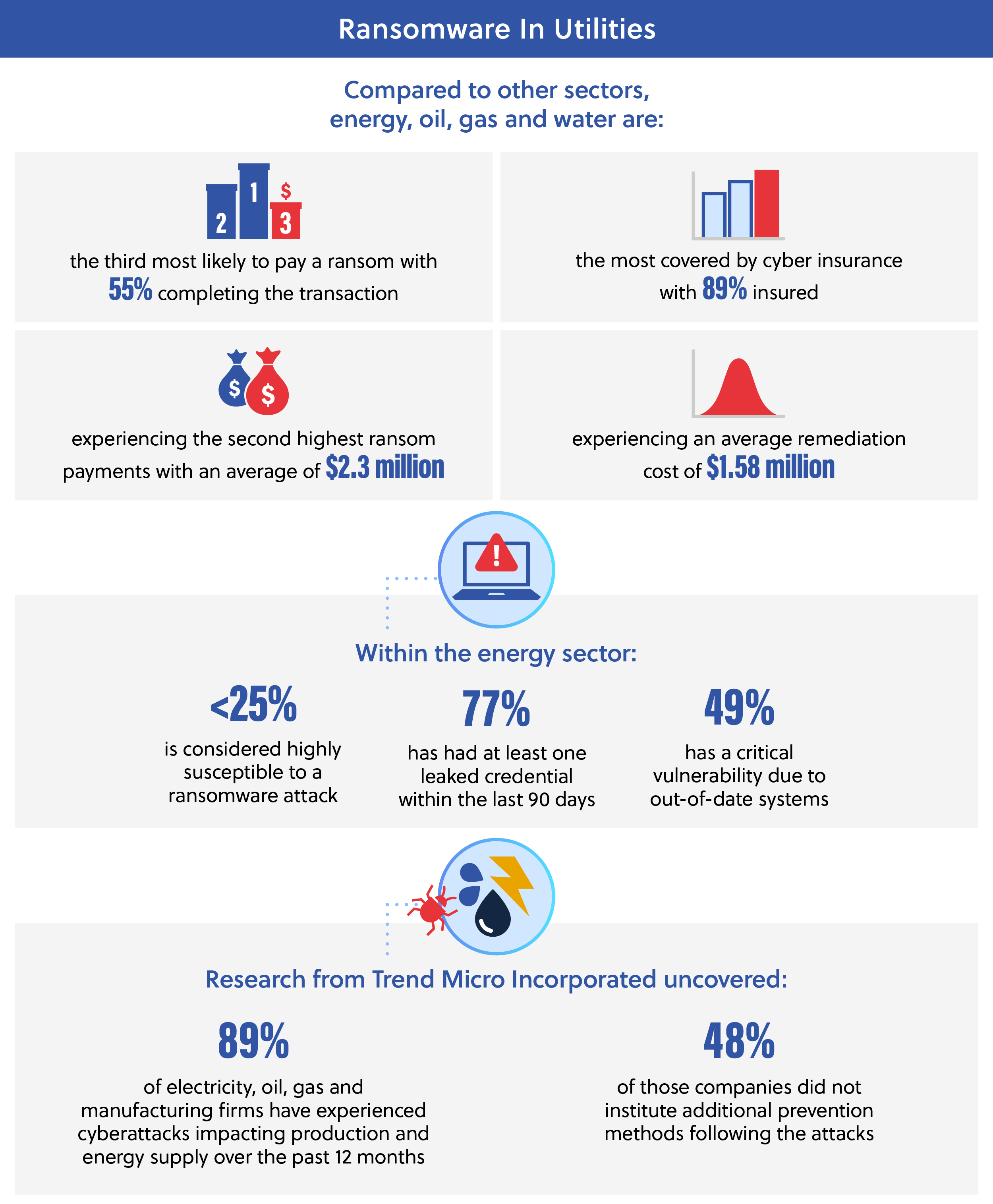
These major attacks in 2021 followed an already heightened evaluation of utilities’ security due to Executive Order 13636, which initiated the National Institute of Standards and Technology (NIST) Cyber Security Framework of 2014,[14a] and the America’s Water Infrastructure Act of 2018,[14b] which required water systems threat risk and resilience assessments to be completed between March 2020 and June 2021.
Post-Attack Measures
Utilities companies often rely on a data backup strategy that replicates the system to a second data center if the primary server fails. This setup works well for natural disasters, but companies must be aware that the infection can also be duplicated on non-segmented backup copies which hackers prioritize attacking as well.
Within the electric power sector, operational technology (OT) is widely spread across data centers’ locations and connected through dedicated cables which allows additional control over networking. This however, increases the attack surface and restricts the network’s ability to adapt and reroute traffic to another safe location in the event of a cyberattack, because the system is hardwired to be isolated.[15] Companies must be careful not to assume the direct lines would be inherently secure and should continue to conduct system monitoring especially as these networks start connecting to other systems. In addition to geographical and system complexities, many utility organizations also have decentralized cybersecurity leadership, which can contribute to post-attack confusion and a lack of clarity on the recovery plan.[16]
While demonstrating the return on investment (ROI) of cybersecurity strategies can be a challenge until an attack has occurred, experts highlight the value of these measures by pointing out the impact that a compromised system can have on a company and the general public.[9] With cybersecurity, success is ultimately demonstrated by the absence of cyber incidents. In the past, this led to a reluctance to invest in necessary cyber measures; however, this awareness is shifting as more companies are joining the initiative to secure their systems and networks.
In July 2022, national security advisors announced additional cybersecurity requirements will be instituted soon by the Environmental Protection Agency (EPA) to defend national water systems from hackers.[17] To prepare for these new guidelines, companies within the utilities sector must evaluate their systems and work to improve their defenses and recovery plans now in the face of ransomware attacks.
LOOKING AHEAD
Critical infrastructure across the country has been overwhelmed by the influx of ransomware and data breaches. Looking at the data projections for the coming years reveals that these intrusions will continue to grow at an alarming rate. While legislation develops to address the current cybersecurity gaps, sectors like healthcare and utilities must actively take initiative to address system weaknesses and make it more difficult for cybercriminals to infiltrate. Investing in the necessary changes and updates is crucial for U.S. critical infrastructure organizations before their individual institutions become the next target. Now more than ever is the time to modernize infrastructure, get ahead of cyber requirements and build resilience against the threat landscape.
Learn about steps to address these cybersecurity concerns whether in healthcare and utilities or across all sectors in our Ransomware Security Strategies Blog. Find our full Ransomware Series here.
Resources
[1] “FACT SHEET: Biden-Harris Administration Delivers on Strengthening America’s Cybersecurity,” The White House, https://www.whitehouse.gov/briefing-room/statements-releases/2022/10/11/fact-sheet-biden-harris-administration-delivers-on-strengthening-americas-cybersecurity/
[2] “Healthcare data breach costs reach record high at $10M per attack: IBM report,” Fierce Healthcare, https://www.fiercehealthcare.com/health-tech/healthcare-data-breach-costs-reach-record-high-10m-attack-ibm-report
[3] “Ransomware attacks on hospitals could soon surge, FBI warns,” CNET, https://www.cnet.com/news/privacy/fbi-warns-imminent-wave-of-ransomware-attacks-hitting-hospitals/
[4] “Ransomware 101 For Healthcare,” Forbes, https://www.forbes.com/sites/forbestechcouncil/2022/08/16/ransomware-101-for-healthcare/?sh=3bb3ca785b86
[5] “The pandemic revealed the health risks of hospital ransomware attacks,” The Verge, https://www.theverge.com/2021/8/19/22632378/pandemic-ransomware-health-risks
[7] “Ransomware in healthcare: it’s a matter of life and death,” NTT, https://services.global.ntt/en-us/insights/blog/ransomware-in-healthcare
[8] “Everything You Need to Know About Ransomware,” Ransomware.org, https://ransomware.org/
[9] “Ransomware Attacks in the Energy Industry,” CDW, https://www.cdw.com/content/cdw/en/articles/security/ransomware-attacks-energy-industry.html
[11] “The Critical Need to Protect Critical Infrastructure: Spotlight on Utilities,” Spy Cloud, https://spycloud.com/protect-critical-infrastructure-utilities-ransomware-ato/
[12] “How Utilities Can Reduce the Risk of Ransomware Attacks,” Energy Central, https://energycentral.com/c/pip/how-utilities-can-reduce-risk-ransomware-attacks
[13] “Ransomware Hits U.S. Electric Utility,” Trend Micro, https://www.trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-threats/ransomware-hits-u-s-electric-utility
[14a] “NIST Releases Cybersecurity Framework Version 1.0,” NIST, https://www.nist.gov/news-events/news/2014/02/nist-releases-cybersecurity-framework-version-10#:~:text=In%20February%202013%2C%20President%20Obama,help%20organizations%20manage%20cyber%20risks
[14b] “What Does the New American’s Water Infrastructure Act (AWAI) of 2018 Mean to You?” Crawford, Murphy & Tilly, Inc., https://www.cmtengr.com/2019/08/20/americans-water-infrastructure-act/
[15] “How energy and utility companies can recover from ransomware and other disasters using infrastructure as code on AWS,” AWS, https://aws.amazon.com/blogs/industries/how-energy-and-utility-companies-can-recover-from-ransomware-and-other-disasters-using-iac-on-aws/
[16] “Ransomware and Energy and Utilities,” AT&T Business https://cybersecurity.att.com/blogs/security-essentials/ransomware-and-energy-and-utilities
[17] “White House Official: EPA to Issue Cybersecurity Rule for Water Facilities,” Nextgov, https://www.nextgov.com/cybersecurity/2022/07/epa-issue-cybersecurity-rule-water-facilities-white-house-official/375098/
Infographic Resources:
[6] “The State of Ransomware in Healthcare 2022,” Sophos, https://news.sophos.com/en-us/2022/06/01/the-state-of-ransomware-in-healthcare-2022/
[10] “Looking Back at the Colonial Pipeline Ransomware Incident,” Government Technology, https://www.govtech.com/blogs/lohrmann-on-cybersecurity/looking-back-at-the-colonial-pipeline-ransomware-incident
“The 2021 Ransomware Risk Pulse: Energy Sector,” Black Kite, https://blackkite.com/wp-content/uploads/2021/09/The-2021-Ransomware-Risk-Pulse-_-Energy-Sector.pdf







